humanID Blog
Cybersecurity Tips for Small Businesses
When a cyber threat occurs unprepared they may feel overwhelmed. Hence, they need to be aware of cyber threats and how to stop them.
Is reCAPTCHA Still Effective in Times of Generative AI?
ChatGPT and Dall-E are becoming advanced, it is only a matter of time before generative AI Google’s current reCAPTCHA system would make it obsolete.
Why Password Logins are Vulnerable to Cybercriminals
Without a doubt, there are many types of password hackings a cybercriminal could consider to steal information.
How humanID’s Login System Improves User Experience
Constantly forgetting and resetting passwords doesn’t have to be the norm, however, if more websites implemented humanID’s password-less login system.
How to Protect Your Discord Server
Here are some ways to protect your Discord server from scams and hackers.
How To Block Comment Spam On My WordPress Page
Check out this list to find out how to block spam from your page, starting from least to most effective!
Why Anonymous Login Helps Your Users Feel Safer
By storing less personal information, starting at the login, users can begin to feel safer knowing that they’ve revealed less information.
How to Help humanID Every Time you Shop on Amazon
AmazonSmile is a fast and easy way to support a charitable organization every time a customer purchases at no extra cost.
Why You Shouldn’t Use Passwords For Your Login
The majority of services still use passwords for logins, they are not as effective in security and productivity as their alternatives.
How to Add humanID’s Discord Bot to Your Discord Server
With Discord’s growing community, humanID can help assure privacy for each user. Here is how to add humanID’s discord bot to your server.
How Do I Install humanID’s Plugin in WordPress?
Want to learn how to block spam bots, spammers, and negative commenters on WordPress? Here’s how to do it with humanID’s plugin.
What Login Should I Use For My New Social Media App
Every user pays social media their login. Let’s explore what elements a good login should have.
How Does Data Mining Affect You?
By 2022 there will be 5,200 TBs of data on every person on the planet. Almost everyone leaves behind enough data that could be mined.
How Can I Make My Users Feel Safer?
How can I make my users feel safer if hostile tactics such as data breaches are out of their control? Data transparency.
Email vs. SMS Verification: Which is Safer?
With Two-Factor Authentication becoming popular in online security, there are questions about the safety of email and SMS verification.
Should My Software Be Open-source?
Open source software is an excellent place to start your software journey if you want flexibility, scalability, and reduced cost.
5 Common Cyber Attacks and How to Prevent Them
From phishing to DDoS attacks to malware, cyber attacks threaten all businesses. Here’s how you can prevent them.
5 Best Alternatives to reCAPTCHA
Guaranteeing more accessible security measures and ensuring a higher level of ease in the anti-spam process will retain more users than a faulty and challenging series of puzzles.
One Human, One Log-In: Why and How
One human, one-login bridges the gap between the real and digital worlds. Ideally, each person holds one digital identity linked to several accounts.
Cybersecurity & Privacy in 2022
Strong data privacy includes understanding data technologies and databases, identifying sensitive data, establishing data usage policies, and controlling access to sensitive data.
Metadata: How to Safeguard Your Privacy
Metadata, as a vital piece of one’s online presence, must be protected to avoid exploitation or manipulation by third parties.
Best CAPTCHAs for Accessibility
Accessibility is too often ignored in our online world. It is crucial for websites to stay vigilant about features that may serve as a barrier to potential users.
How to Build User Trust
Building user trust is crucial to achieving your website or app’s long-term goals relating to growth, product development, authenticity and reputation, and consumer safety and satisfaction.
Importance of Cyber Privacy: How Safe is Your Data?
As quintillions of bytes of data are being gathered on the internet daily, it is necessary to make sure to protect information from the “data hunters”.
How Do I Prevent Cyberbullying on My Platform?
In modern times, cyberbullying is no longer an uncommon phenomenon. It is bullying that takes place through the use of modern technologies, and is intended to constantly frighten, anger, or humiliate those victims who are being targeted.
The Internet of Things (IoT) and Maintaining Cybersecurity
Internet of things, IoT, are physical devices around the world that are connected to the internet, collecting and sharing data. IoT protection is necessary, it is useful against botnet attacks, DNS attacks, ransomware, and shadow IoT.
5 Top-Profile Data Breaches in 2022
The Identity Theft Resource Center recorded 1,862 overall data breaches in 2021. Here are five top-profile company data breaches in 2022 thus far.
The Need for Open-Source Identity Management (IAM)
Identity and Access Management, or IAM, is the digital perimeter of today’s business; robust authentication protocols can help keep digital content safe.
How to Comply With the Utah Consumer Privacy Act (UCPA)
New Utah legislation is poised to join California, Colorado, and Virginia in improving US data privacy measures. Here’s what to know about the Utah Consumer Privacy Act and how to comply as a business.
CAPTCHA: The Conversion Rate Killer
While CAPTCHAs are used to block bots and spam on websites, there are instances where real users are blocked as well, affecting conversion rates.
Is Security More Important than Privacy? No: Here’s Why
Security and privacy: which is more important? They are frequently looked at as two sides of the same coin, but this is not necessarily the case.
3 Cybercrime Cases to Make You Reevaluate Your Cybersecurity
Protecting your information by rethinking your current cybersecurity and privacy protocols will help mitigate cybercrime cases.
8 Ways to Minimize the Risk of Data Leaks
Data leaks can expose customer information and precious company data. Do not leave your information in the open for attackers—here are 8 ways to minimize the risk of data leaks.
humanID Partners with report it® to Enhance Crowdsourcing Anonymity
humanID is proud to announce our newest integration with report it®, a nationwide whistleblowing and crowdsourcing website now offering humanID.
Best Two-Factor vs. Multi-Factor Authentication Options
Fortunately, there are numerous two-factor and multi-factor authentication tools that mitigate such security risks brought on by digital transformation.
Can CAPTCHA Prevent CSRF? Not by Itself.
CSRF, also called XSRF and pronounced “Sea-surf”, is when a malicious entity takes advantage of an authorized web session and submits requests to the server while posing as the authorized user. CAPTCHA is a type of User Interaction (UI)-based CSRF Defense. CAPTCHA cannot prevent CSRF attacks by itself, and its implementation as UI-based CSRF Defense can leave users open to attack.
Flutter Login SDK
Software Developing Kits, or more commonly known as SDKs, are tools that allow programmers the ability to develop applications on different platforms and operating systems. There are many tools alike, but one that stands out is Flutter, which is a login SDK tool developed by Google.
How to Improve Data Visibility
The methods with which we manipulate and analyze data are being held to higher standards. If used correctly, organizations that improve their data visibility can enhance their security and improve efficiency.
HIPAA-Compliant Login: The Law and the Tech
HIPAA’s principles of flexibility, scalability, and technology neutrality give covered entities and business associates leeway on login implementation. Though navigating them can be like opening a can of worms. What can one do to construct a HIPAA-compliant login?
Comparing Auth0 and humanID
With SSO, the service offers many different solutions to meet modern expectations of privacy. This article will look to solutions Auth0 and one of its alternatives, humanID.
8 Best Whistleblowing Sites
Whistleblowers are individuals known to expose information deemed illegal or immoral. Join us in a tour of the best whistleblowing sites of past and recent times.
Family-Friendly Single Sign-On
The internet can be a dangerous place. A single sign-on can ensure a family-friendly web experience and put a lot of parents at ease when their children log in.
How to (Not) Get Hundreds of Burner Numbers
Registration allowing burner numbers can seemingly spell trouble if attackers were to carry out a distributed denial-of-service (DDoS) attack or similar on a digital platform. In practice however, obtaining a mass amount of burner numbers is a more difficult task than it appears to be.
How SSO Makes Being HIPAA Compliant Easier
Even with data that is not as important, a breach can enable many bad things to happen: the HIPAA act was enacted to combat this by improving security when handling PHI and ensuring that affected individuals are aware of a data breach.
What is Cyber Spying?
When presented with the term “spying”, what comes to mind? You may picture someone lurking in a dark alley, or blending into a crowd, watching a target from afar to document their every move. Within the past few decades however, this stereotype is not as applicable. Nowadays spying is primarily carried out online through a practice known as cyber spying.
5 Privacy Steps for Better Cyber Security
Cybercrime increased by an alarming 400% in 2019 and 2020 combined. What can one do to understand cybersecurity risks and better protect their privacy in a constantly changing digital world full of data leaks, ransomware, and social engineering?
The Do’s and Don’t’s of Cyber Security: Passwords
So, you might wonder, how could I protect myself from the consequences of data breaches and keep myself secure in the ever-growing digital world? For this, here is a consolidation of four cyber security password tips for you to analyze if your information is genuinely safe.
What is Cyber Insurance and Who is Getting It?
Within the last year, multiple breaches have occurred leaving the data of ordinary people vulnerable to theft. Almost 10 billion online records from various sources were breached in 2019 alone. This has led insurance companies to offer cyber insurance.
User Authentication Methods
Authentication means a website can prove that the person accessing their site is who they say they are. There are a few choices developers can implement to authenticate users. What exactly are those methods?
Improving Sign-Up Page Conversion Rate with Single Sign-On
The average website conversion rate for sign-ups equates to only 2 to 5 percent. There are a few reasons for the low nature of this average, but luckily there is a method a business can put into place to improve their own sign-up page conversion rate.
SSO: A Scope of Solutions
Single Sign-On (SSO) is an authentication service that permits a user to use one set of login credentials instead of using multiple certificates. Multiple credentials, such as passwords, can be cumbersome to login to various accounts. Other features of logins such as anonymous logins or alternative logins act as safeguards for when these passwords become forgotten, but SSO resolves the conflicting nature of multiple login implementations while being bot-resistant.
Websites Stalk Us
Websites use cookies to track user data. This occurs even without a login. A cookie is a collection of information about your activity on any given website. The information typically contains your IP address and their habits on that site. Websites collect these cookies even without a user needing to login. Every time you access a site the cookie, or cookies, is updated with new information.
Can CAPTCHA Be Hacked?
If you frequent the internet, you are likely familiar with the requests to select all the squares containing stop lights or to re-type a distorted word. These requests are examples of CAPTCHA, a system used to verify a user’s humanity before accessing a digital account. Since its release in 2007, CAPTCHA tasks have become more complicated to compensate for advances in artificial intelligence (AI) technology and its ability to learn how to crack these tests.
How to Prevent Spam Without Traditional CAPTCHA
CAPTCHA is not the most effective way to prevent spam. On top of being difficult for humans to decipher, most spam bots can decode these cryptic messages with ease. The Completely Automated Public Turing Test to Tell Humans and Computers Apart (CAPTCHA) is outdated. If traditional CAPTCHA was true to the original Turing test, the onus of proof should lie with the machine, not the human.
Data Breaches of 2021
Data breaches are nothing new in the online world. Feeling unsafe online is, unfortunately, the norm for most. While a company’s reputation may be ruined for the time being, the most important thing is that people’s personal information is put at risk because of the trust they place in companies. In just the second quarter of 2021, data breaches have increased by 38 percent compared to the first quarter.
3 Reasons to Consider Passwordless Single Sign-On
How often do you use the same password for your online accounts? For memorization’s sake, it is definitely tempting to reuse a password for more than one digital account. This is especially true if you are convinced that it is a strong enough password to not be cracked easily. However, just one data breach incident could allow access to the entirety of your internet activity.
React Native Login SDK
A few decades ago, creating an application and integrating it with features such as authentication and user management was time consuming, and in most cases came with a high cost. In short, it was not always easy to make an application. As of now, a single developer can create, integrate, and finalize a whole application in a matter of days or up to weeks depending on the complexity of the project.
How to Detect Data Leakage
With an increase in remote work and internet activity, data leakages have never been more common than in this past year. Online data is frequently at risk of being used to cause personal, financial, and reputational damage to individuals and businesses. Thus, it is important to understand how data leakage works in order to implement the right prevention methods.
How to Recover From Cyber Attacks
Cybercrime occurs much more often than you think. A 2018 Gallup poll revealed that a quarter of American adults have experienced cybercrime. Perpetrators of so-called cyber attacks exploit businesses with weak security and less tech-savvy individuals. These numbers rise in parallel with the world’s increasing online presence, especially due to the recent pandemic.
Captcha Alternatives for Mobile Apps
Are you a bot or a human user? It is essential that applications know the answer to this question to keep out ill-intentioned users, scammers, and bots. Failing to do so could result in fraudulent activity, scans of software vulnerabilities and malicious attacks.
Are Popular Apps for Children COPPA Compliant?
Apps are a part of our daily lives. However, convenience may come at the cost of online safety. While this is unfortunate, it is not uncommon. This in turn impacts vulnerable groups, one of the most vulnerable being children.
What Does It Mean to be HIPAA Compliant?
The Health Insurance Portability and Accountability Act (HIPAA) is a set of regulations that dictate how to lawfully use and disclose individuals’ protected health information (PHI). The Department of Human Health and Services mandates that all covered entities and business associates operate in compliance with HIPAA.
Open Source SSO Solutions
User authentication is one of the services that every website or online business should offer. Regardless of the implementation, the authentication must be safe and secure. Users could be authenticated by using credentials such as email, password or phone number. Yet, this diversity of credentials could result in inconvenience and is susceptible to malicious entities.
How Valuable Is Your Data?
As our lives increasingly integrate with the internet, the risks of exposing our personal data also rises. Most of your online interactions such as clicks, purchases, and social media likes are valued in the market and often used to exploit your online habits.
Why SSO is Relevant
If you have more than a few passwords, then I’m sure you have had to click that “Forgot Password?” message recently. And, unfortunately, you probably had to go through all your email accounts to locate the one linked for this specific platform, scan through your spam, and log back into your account with a new password you might forget once again. Single sign-ons (SSOs) aim to limit this password fatigue by providing an efficient alternative
Defining Hashing and Encryption
Hashing and encryption are two common methods that are imposed to enhance digital privacy. It is necessary that enterprise users understand the purposes, functions, capabilities and limitations of each method.
What are Identity Providers?
For every service that people use in their daily lives, being identified as a legitimate user is a must to have access to the service. To identify a user, businesses use a set of credentials such as username/password, email, phone number, PIN code, and others.
A Guide to Privacy Policies for Minors
Technological advances have brought about detailed privacy policies. Over the years, privacy policies have been used to ensure company transparency about their data collection. Data collection and data mining are prevalent issues, especially in the US.
How to Stop Spam Comments
How to Stop Spam CommentsBy Quan Nguyen September 3, 2021 If you have spent some time on the internet, you most likely have come across spam comments. It is almost impossible to visit sites including comment and interactivity features without encountering spam. In...
Why Your Business Should Implement Single Sign-On
Single Sign-On solutions (SSOs) offer an opportunity to ease the navigation of the internet for users. They can resolve various complications often encountered by corporations, such as frequent password resets and CAPTCHA’s nuisance. As businesses and consumers become increasingly dependent on technology, most users have encountered these difficulties in some capacity.
Priest Resigns After Lack of Privacy on Grindr
This month, humanID has been cooking up a lot of new projects and the tech world has made a lot of questionable decisions regarding privacy and anonymity. Keep reading to see what new things we have released in the last month. Don’t forget to reply back to this email and let us know what you think of all the new releases!
How To Protect Yourself From Being Tracked Online
There are a few things that simultaneously happen each time you log into your browser. Your data is accumulated, aggregated, and put to use in ways that are unbeknown to you. Even something as trivial as the meme you shared with your friend can be accessed and used to extract a piece of the puzzle that is your online identity.
How to Protect Your Online Information
The pandemic has created a lot of issues, both in the real and virtual world. As a result of increased remote work and online activity, cybercrime has risen an alarming 400% in 2019 and 2020 combined. Ransomware also rose 69% in 2020.
How to Stop Spam Email Submissions
If you have an email address, surely you have dealt with spam email submissions. Spam messages come from illegitimate email addresses and usually contain malicious intentions. In fact, 320 billion spam emails are sent daily; 94% of malware is delivered via email spam messages.
Should you use email or phone number authentication?
Email authentication and phone number authentication are two widely used authentication methods that are said to protect people from hackers and other cybercriminals; but, they potentially make it easier for cybercriminals to invade user privacy and protection.
Top Five Single Sign-Ons
In this day and age, people have become increasingly wary of online privacy. Something seen in the U.S. where at least 75% of Americans say they want increased government regulation regarding data use by companies. This may not come as a surprise for most people given alleged reports on data mining from large multinational corporations (MNCs), like Target, Amazon, Facebook, and Google.
Pros and Cons of Single Sign-Ons
The internet has expanded to the point where we have accounts for everything. Whether you are shopping online, checking mail, or even watching videos, you are likely signed into some account. The process of signing into several accounts daily may prove bothersome and inefficient. Single Sign-On (SSO) services aim to reduce the number of logins you have to perform, but are they secure?
How to Stop DDoS Attacks
Hackers are always a step ahead of security measures. As data security quality increases, malicious entities create new methods to outperform those security measures. One of the most common attacks on the internet is Distributed Denial of Service (DDoS).
Is Data Privacy a Sacred Duty for Muslims? 🙏
What do the health sector, faith, and Congress have in common? Digital privacy! Or, well, problems when that privacy is violated. Read on for the latest on digital privacy breaches, some great tips on bot detection, and whether you should implement SMS authentication, from your friends here at humanID.
Malicious Life and humanID: A Better Internet
The internet is plagued by data collection, data leaks, bots, hacking, and disinformation. Large corporations, such as Google, Facebook, Apple, Amazon, and Microsoft, collect and monetize the data they gather from users. This is because data is highly versatile and profitable, making it the most valuable asset in the world.
How to Detect Bots
Many online activities, such as playing video games and reading tweets, include the use of programmed bots. A bot is an automated software program that is used to make HTTP requests and to perform repetitive tasks efficiently and consistently. Tasks that programmed bots facilitate include filling out forms, clicking on links, listening to music on Discord, posting on websites, and many more.
Should I Implement SMS Authentication?
Passwords are terrible at verifying identities. Computers cannot differentiate who is typing an alphanumeric password, so anyone with the information can authenticate themselves as another user. With the majority of people having some SMS–capable device, it is imperative that we transition away from solely using passwords.
How does Big Tech use data mining?
All of Big Tech collects a lot of data and utilizes data mining; consequently, these businesses become valuable assets in the global economy because collecting user data generates large earnings. After Facebook’s employees had developed apps for its business in 2008, they became very financially successful.
EA Games Source Code Taken By Hackers 🎮
The last month has been buzzing with news on privacy and misinformation while your friends at humanID have been busy putting out a lot of new content. Let’s look at what’s fresh at humanID and with the rest of the industry.
How do I implement Email Authentication?
Signing into a new platform like Facebook, Amazon, or Google is easy. With one click, you can enter the site with just your email. The website receives all your personal information and data, and you get to use the services the website provides. Many users are unaware of the policies they approve of when they sign into these platforms, as well as the third parties the user’s email address makes contact with.
How Safe are the Top SSO Solutions?
Single Sign-On solutions (SSOs) have become increasingly popular as concerns over cybersecurity and online privacy continue to grow. SSOs simplify the login process by eliminating the need for passwords. They generally increase security and protect user privacy as cybercriminals typically target usernames and passwords. Consequently, every time someone logs into a new account, a new opportunity for an attack is possible.
Best Ways to Prevent Data Loss
Personal data is constantly becoming more easily accessible and thus more susceptible to cybercrimes like data breaches. Personal data can include social security numbers, credit card information, as well as past and current addresses. Not only can data losses cause extreme privacy issues for individuals, but also mass financial and reputational complications for businesses.
How To Do Away with Passwords
How many passwords do you have? You likely have more than you can remember. In fact, users often have upwards of 90 online accounts and reuse 51% of their passwords. If you can remember all your passwords, it is likely that you reuse a portion of them, which is a serious risk for losing personal information. As more businesses are connecting to their users through online accounts, username and password combos are rising while password reliability and security are decreasing; anyone can access your account with the right credentials.
TikTok’s New Third-Party Integrations Create Privacy Risks
Assisted by the pandemic and the increasing interest in technology, internet reliance is more prevalent now than ever. Accordingly, TikTok, a video-sharing platform, has seen a surge in popularity these past few years. TikTok’s algorithm and ability to bring new and smaller content creators to the surface makes the app unique and popular. And while the platform’s influence has empowered many younger generations and grown as a whole, TikTok’s recent expansion of integration with third-party apps may have overstepped the boundaries of its power.
5 Alternative Authentication Types
Password-based authentication methods can easily be done through phishing attacks. This leads to many users not protecting their passwords. Indeed, just 54% of users use five or fewer passwords for their accounts because they do not think that people are going to gain entry into their accounts. Authentication is useful because it prevents infiltrators from accessing databases, networks, and other resources.
How Companies Can Improve User Safety
During a time in which there is a rising prevalence of user safety attacks, only 20% of Americans totally trust the organizations they interact with to maintain the privacy of their data. More importantly, out of the 80% of Americans that do not totally trust these organizations are a lot more concerned that hackers will access their data than companies using it without their permission.
Courts Force Disney to Stop Collecting Children’s Data 🧙
This past month saw promising headway made in the privacy space. There were critical steps taken in AI governance, a settlement by a big-name company regarding the handling of children’s data, and attempts by an internet giant to revise its website tracking technology.
What are COPPA App Guidelines and Why Do They Matter?
While we stand at the peak of technology, applications on computers and smart devices threaten children’s privacy and security. With the mass production and distribution of digital devices to most of the world’s population, the internet is becoming increasingly accessible.
Can CAPTCHA Prevent DDoS Attacks?
With the increasing reliance on the internet and technology comes the risk of malicious attacks and data breaches. While some attacks target everyday citizens and consumers, other attacks focus on information technology companies, e-commerce businesses, government agencies, and more.
How does Single Sign-On Work?
With the rapid growth of the internet and technology comes the risks of privacy protection and cybersafety. Passwords are one of the simplest security devices the internet utilizes for use protection. However, many believe that the password has become outdated and less effective.
What is Data Scraping and is it Illegal?
Generally, data scraping refers to the extraction of data from a computer program with another program. Data scraping is commonly manifested in web scraping, the process of using an application to extract valuable information from a website.
reCAPTCHA: How Much Will We Give Up for Security?
As so eloquently put by John Mulaney, “The world is run by computers, the world is run by robots and we spend most of our day telling them that we’re not a robot just to log on and look at our own stuff.”
The True Cost of Cybersecurity for Small and Medium Businesses
According to some estimations, the global cost of cyber attacks in a year could total up to about $1 trillion, over 1% of the global GDP. Such a high number should not be surprising to most readers.
How can SMEs bolster their cybersecurity?
Cybersecurity isn’t something only large, high-profile corporations that handle large amounts of sensitive data should worry about. From conception, any modern enterprise will need to plan on investing in a multitude of security measures to mitigate a growing array of cybersecurity risks.
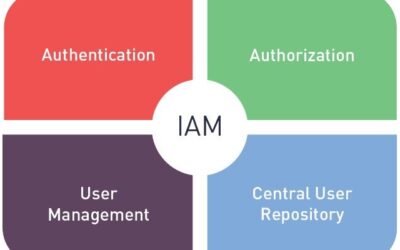
Defining IAM and IGA
IAM and IGA are two of the most common methods for identity management, and it is important for enterprise users to understand the purposes and functions of each system, as well as the benefits and limitations.