Importance of Cyber Privacy: How Safe is Your Data?
By Gyumin Park
July 20, 2022
As quintillions of bytes of data are being gathered on the internet daily, it is necessary to make sure to protect information from the “data hunters”. Commonly known for carrying out cybercrimes, hackers target a network or a networked device in order to access people’s information. Cybercrimes can be in different forms such as email fraud, identity fraud, ransomware attacks, and theft of corporate data. Although punishment for cybercrimes has increased recently, it is difficult to catch these slippery hackers that leave little to no evidence. Thus, many are still looking to find an adequate solution that would secure their cyber privacy.
What types of cybercrimes are there?
Even though the internet world has been vastly expanding in recent years, the types of cybercrimes that occur have not changed much. The most frequent cybercrimes are extortion, identity theft, personal data breach, non-payment, and phishing.
Extortion
Cyber extortion is when cybercriminals access a company’s private data and threaten to release or compromise the data unless they receive a payment. Extortion usually targets small businesses with vulnerabilities in their cyber security.
Identity Theft
Identity theft occurs when cybercriminals acquire an individual’s private identifying information and use it with malicious intent, usually for financial gain. The information they mainly target for include a user’s bank account number, Social Security number, and credit card number.
Personal Data Breach
Personal data breach refers to any breach that leads to accidental or unlawful destruction, loss, alteration, or unauthorized access to personal data. Personal data breach may occur deliberately or accidentally.
Non-payment
Non-payment describes items that are already shipped but not paid for or items that have been paid for but not delivered. In order to avoid non-payment, users must purchase using reliable websites and make sure to keep the receipts and the tracking number in order to identify their package.
Phishing
Phishing can include cybercriminals sending emails imitating large companies in order to gain private information such as passwords and credit card numbers. Some common phishing scams are tech support scams, infected attachments, social media messages, and CEO fraud scams (targeting employees while imitating the CEO).
How often do cybercrimes occur?
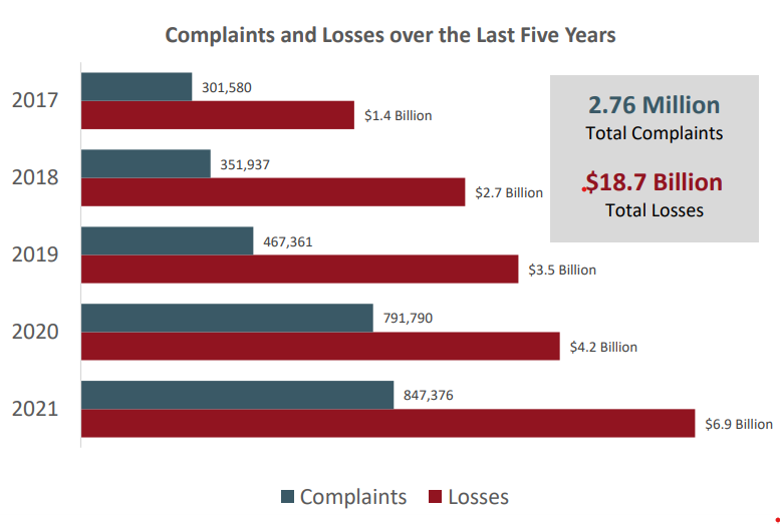
Many individuals or organizations may underestimate the frequency and severity of cybercrimes, but the consequences are costly. According to the 2021 Internet Crime Report released by the Federal Bureau of Investigation, over the last five years, 2.76 million of cyber crimes and $18.7 billion of total losses have been reported.
As shown, the number of cybercrime complaints has almost tripled in 5 years. What stands out the most is that the value of total losses has increased by 5 times over the 5 years. Considering that the most frequent crime types are extortion, identity theft, personal data breach, non-payment, and phishing, which usually do not result in high losses for individual users, this number may seem unusually high. This is because cybercrimes against big corporations result in significant losses.
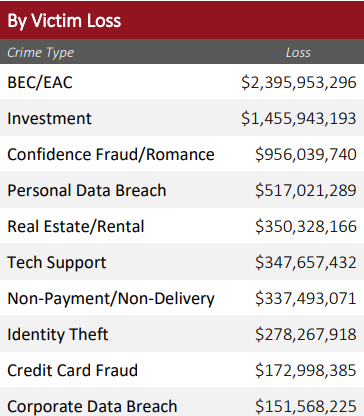
The 2021 Internet Crime Report displays that Business Email Compromise (BEC) and Email Account Compromise (EAC) alongside investment are the two biggest crime types that result in the biggest loss. Even though most cyber crimes target personal data, the ones that result in the biggest consequences are the cybercrimes targeting big businesses and organizations. Recent studies suggest that 83% of small and medium-size businesses are not financially prepared to fully recover from a cyber attack, yet 91% of small businesses have not purchased cyber liability insurance. This is the reason why there is a sharp increase in the number of businesses that are looking to strengthen their cyber security.
How can you protect your cyber privacy?
The most effective way of preventing cybercrime and losses as an organization is by using a password management application or an internet security software that will keep the database and accounts secure. One authentication method that can help is Single Sign-On (SSO). SSO allows users to access multiple applications using one credential which results in increased security and efficiency. Most of the reputable companies such as Google, Twitter, and Facebook have already implemented SSO for enhanced convenience and security. There are also many different types of SSO such as Auth0, OneLogin, and Keycloak which allow businesses to find the perfect SSO that fits their intentions.
One SSO that may particularly help in strengthening cyber privacy is humanID. humanID is an anonymous authentication system that prevents bots and spam. humanID uses an irreversible hash system using the user’s phone number as the authentication method. Once the user is successfully authenticated, the user’s data is immediately deleted. This type of authentication system can prevent information leakage in case of a cybercrime such as data breach as no user data is stored within the humanID’s system except the hashes. humanID can be a great way to protect an individual or a company’s cyber privacy.