FAQ
Q. How does humanID work, in simple terms?
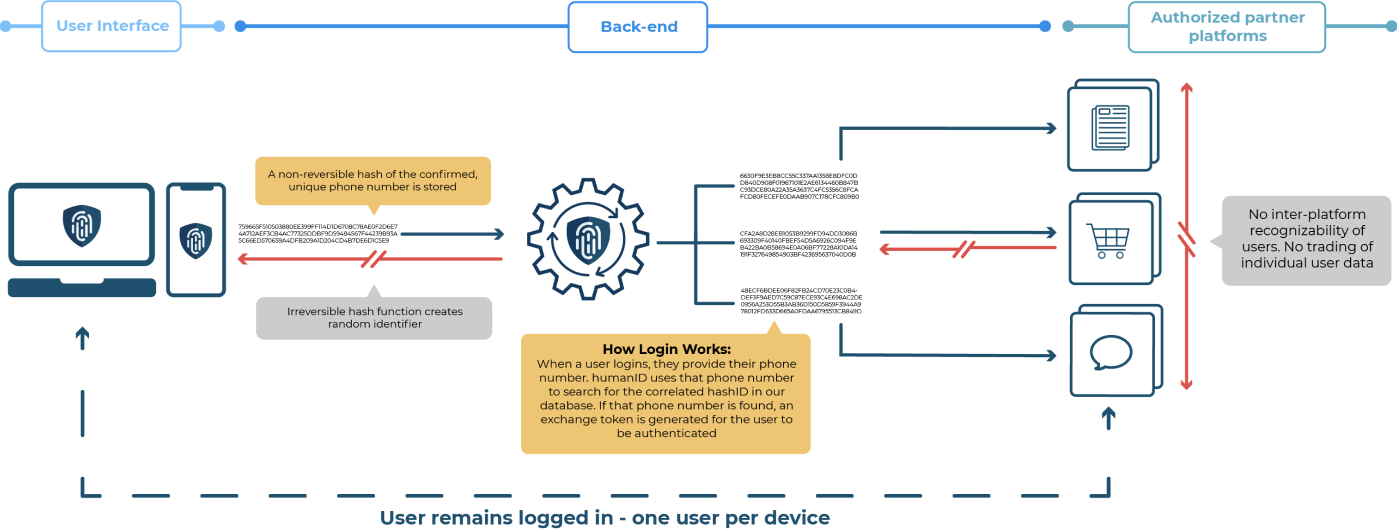
humanID login uses two levels of encoding.
When a user logs in, we first verify their phone number, before hashing it, and deleting it. This hash is the humanID, an ID that doesn’t leave our servers.
When a user logs into a service , we generate a “second-level random identifier” from their humanID and key that is unique to this service. That ID is what we send to the service to identify the user.
Private: This means every service receives a different random identifier when the same user logs in – humanID creates data “silos” that are entirely useless if leaked and can only be used to recognize a user in this specific environment.
Accountable: In the meantime, bots and abusive users will have to get access to one unique phone number to create a new account. Once blocked, this account would be unable to log back into the specific platform from which they were blocked – unless they buy an additional number. We also try to make it less convenient and more troublesome to run several numbers from one phone device – always focused on adding cost and friction for both sophisticated, large-scale bot attacks, as well as unsophisticated trolls and bullies.
humanID CAPTCHA works with existing sign-on services. Users faced with the humanID CAPTCHA send their phone number to humanID (and only humanID). humanID sends an SMS code to this number, verifies that the human has entered the correct code, and deletes the phone number. humanID then tells the website that the user is human, and sign-on is complete!
As a trusted 3rd party, humanID lets websites verify the humanity of their users through phone numbers without jeopardizing their privacy.
Either way, privacy is ensured and abusive behavior managed!
Show me:
Live demo of the fully functional product on web:
https://web-login.human-id.org/demo/
Video Demo:
https://www.youtube.com/watch?v=R8EFWL91628
Last updated: June 2020
Q. Is humanID’s login really anonymous?
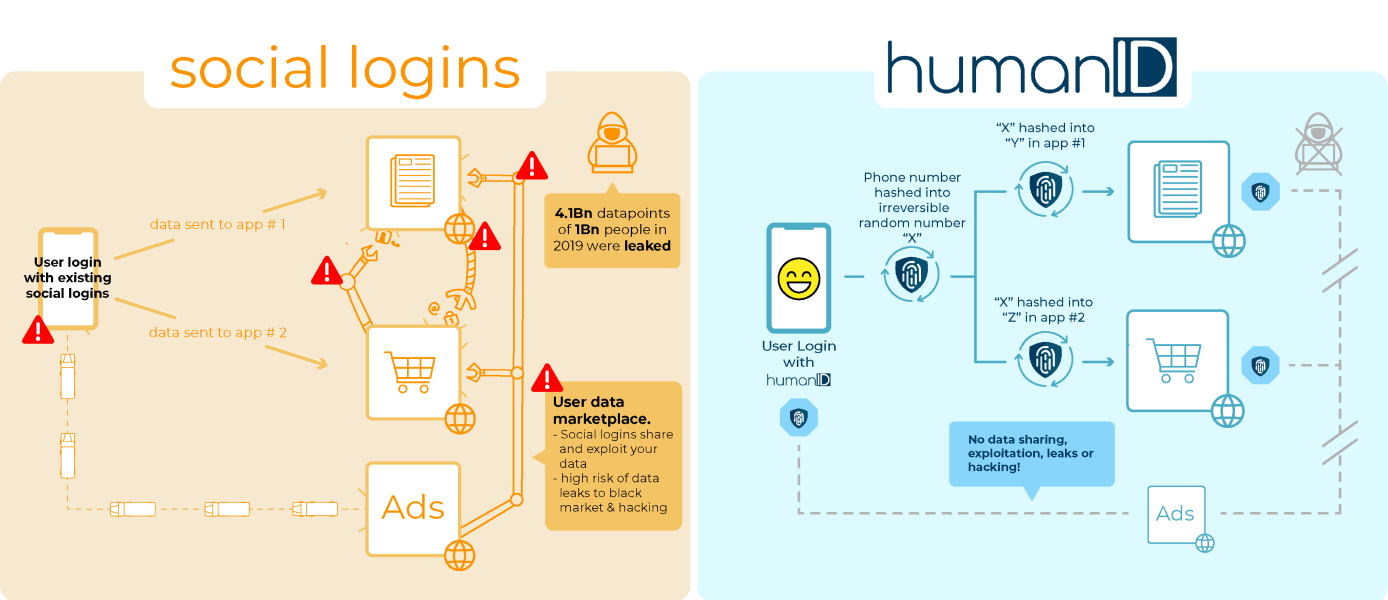
humanID initially verifies your phone number, to ensure you’re a unique user. During this minute, you’re not entirely anonymous. But we then delete your phone number and only save a random identifier (“hash”) as key. We then give platforms yet another random identifier as your identifier – this way each platform knows you under a different identifier, and they cannot mix and match your data.
For platforms, you are entirely anonymous when you enter. And for humanID, we have no way of recovering your information once you’ve verified your phone number.
Note: Platforms can still ask you for your information separately, and this data is not protected by humanID (that might be something we’ll work on in the future!). For example, smartphone applications could ask for your geo-location. We also don’t counter cookie-based identification. If you still encounter “creepy” ads following you around, you might want to consider moving to a privacy-enabled browser, or enabling an ad-blocker.
Q. Why is humanID more secure & trustworthy than other options?
We don’t store any of your information on our servers, or communicate it to the applications you’re using. Our data is hashed in a way that cannot be reversed, so even if our database, or that of our partner applications is leaked, it will not be of use to any malicious actors. It will also be impossible for governments or other actors to identify your real-life identity, or get your phone number.
If a hacker were to access our servers and extract both database and separately stored ‘salt’, the attacker would still have run an extremely costly brute force attack to attain user information. And even that user information would only be of any value to attackers if they also cracked one of our client’s databases.
Q. What information do platforms receive when I log in?
Platforms receive only two pieces of data:
(1) A unique, random identifier (not the hash itself, as that would be more costly to store)
(2) The only other data we communicate and save is the country-code of your phone number (e.g. +1 for US/CA), so communities can adjust their offering accordingly, for example the language.
That’s all.
Q. Can platforms still ask for users’ email addresses, or other data?
Yes! We believe in the empowered user, and there are valid reasons to ask for email-addresses, phone numbers, etc. such as when a user asks to receive a newsletter. But the users will be aware that they’re handing over their data, which most people are not when using a Social Sign On (SSO).
Q. What if I change my phone number and it’s reassigned? Does someone else get access to all their accounts?
Though a user’s humanID account is linked to their phone number, a user in this situation would not have to worry about the new owner of their old number getting access to their accounts. A phone number takes 90 days to be reassigned, and humanID accounts are deactivated after 90 days of inactivity. A recovery email system is in development in case of an accidental deactivation.
Q. Does humanID allow a user to use their accounts on multiple devices?
Absolutely. If a user logs in using a computer (or other device), humanID still sends the verification to the phone number linked to their account. So as long as the user has the associated device handy, logging in on multiple devices is easy.
Q. Does humanID allow multiple accounts on one device?
No, because only allowing one account per SMS-associated device increases the cost of bot networks and allows our clients to more easily permanently ban bots and abusive users.
Q. Does humanID ban users?
No, we do not issue general bans on phone numbers. If a client wishes to ban a user from their site, that is done entirely without notifying us. The user would still be able to log into the website using their humanID, then would be prohibited by the client from accessing their account upon login.
Q. What happens if I don’t have access to my phone?
If the user doesn’t have access to their phone (or to their messages via a browser etc), they could not log in using humanID. The phone access is a key element of protecting platforms from automated and artificial users.
Users could likely continue using products they are already logged into, depending on the partner’s security settings. Compare to how the WhatsApp app requires a phone verification at first login, but can be used freely afterwards.
Q. What’s hashing, how does it work, and how is it different from encryption?
Hashing applies a ‘formula’ to a ‘message’ (such as your email address or your phone number), and transforms it into a very long, random jumble of letters and numbers. This link provides an example of a hash. The same message will ALWAYS generate the same “hash”, or jumble of letters and numbers, but it’s IMPOSSIBLE to get back to the original message simply by looking at the hash. Codes are unique, yet anonymous.
Encryption is a two-way function, but requires a special ‘key’ to revert the message back. Hashing is one-way only. For example, iMessage and Whatsapp use end-to-end encryption for messaging, because you do want to be able to read the texts a friend sent you. We use hashing, because nobody should ever be able to decode your personal information.
Q. What does open source mean?
This means that our code is made freely available and can be redistributed and modified. Most for-profit companies keep their code highly protected and will seek out patents for IP protection as well. We believe that our mission aligns with an open source code, developing our structure in a trusting and collaborative way.
Q. Since data for many businesses is revenue, what will make them want to use humanID?
You can still ask for user data! You would just have to ask after the login step so that the user is fully informed that their information is being collected. Users appreciate this as well. When you contact them, they’ll know how you got their information. They’ll trust you more, and they’ll be interested in the information you’re sending them. That way, when you send information, you can be sure that users are actually reading it, and they’ll appreciate and trust your asking for permission.
For many businesses, we make up for it in cost of privacy breaches, aggregated data, cost of bots and spam. 90% of spam and abuse come from previously banned accounts, for example. Additionally, aggregated data is often only marginally less useful than individualized data.
Legislation is also trending towards upending the status quo for data collection.
Q. What percentage of users do you think will opt for humanID if offered in parallel with other logins? How does humanID improve my conversion rate?
While initially – with low brand recognition – only a low double-digit amount of users choses humanID vs competing Social Sign-Ons, what is more important is the effect on the overall conversion rate. humanID’s promise of anonymity has a very high appeal to the ~25% of the population that are extreme users of privacy-first tools such as ad-blockers, VPNs and cookie blocking technology. This means many of the humanID users are marginal logins that would otherwise not have converted out of privacy concerns.
In addition, humanID makes the use of RECAPTCHA and similar technology redundant, as bot users are already excluded upon signup. This, as well as the added feeling of security and privacy, will also increase your engagement rates and lead to higher willingness to share and participate from the end user.
Q. Do people have to go through the SMS verification process every single time they login?
They do not, unless you choose to make them. Users must only go through the SMS verification process for first time users/account creation
Q. How is humanID different from email and phone number verification processes? If humanID is similar to SMS but with a 20-30% price increase, what’s the value added?
humanID does NOT store any user data any longer than needed. The phone numbers given are deleted after 15 minutes maximum. As a nonprofit, humanID lacks the incentive to sell user data. The value added by humanID is our commitment to providing complete privacy for a user and our ability to filter out fraudulent accounts and bots.
Q. Does user privacy really matter? I haven’t detected that my users dislike Login with Facebook?
Yes it does! User research shows that the “Privacy Paradox” (~ Users say they care, but don’t act like it) is a myth.
One poll found that many people take a dim view of those “targeted” advertisements. Some 63 percent said they would like to see “less targeted advertising” in the future, while 9 percent said they wanted more. When asked to compare them with traditional forms of advertising, 41 percent said targeted ads are “worse” while 21 percent said they are “better.”
https://www.reuters.com/article/us-usa-facebook-poll/americans-less-likely-to-trust-facebook-than-rivals-on-personal-data-reuters-ipsos-poll-idUSKBN1H10K3
66% of people said data-privacy concerns impacted their trust of social media. Only 13% of respondents said “don’t care,” while 17% said that the impact of data privacy issues on their social media attitudes was “low.”
https://marketingland.com/more-people-trust-and-distrust-facebook-than-any-other-social-site-survey-269130
Q. What if I already have some secondary authentication measure (i.e. I might use RelevantID)? Is humanID complementary? Is it better?
Complementary, but has better security than other login services. It’s also just as easy.
Q. We already have a comment moderation, flagging, and blocking system. Why isn’t that sufficient?
Moderating comments can only go so far. Banning users does not prevent them from creating new accounts and continuing their behavior. humanID prevents people from returning by requiring phone numbers, but with its convenience, it doesn’t hurt conversion (in fact it helps).
Q. If we block a user, aren’t they gone? Why do we have to worry about returning abusers?
No! They can just create another email and continue to harm your platform.
Is it possible for them to get a second phone number?
Perhaps, but it’s very difficult. We raise the costs of continued spam and abuse by substantial margins, which keeps bot armies and mass attacks away. I talked to a mid-sized social network, which acknowledged that based on IP address and phone fingerprinting, they see the same abusive users creating 20 and more accounts to spread their posts. Facebook deleted more than 7 billion fake accounts last year, which shows the scale to which this problem can grow, especially if Lokal continues to grow. Chances are not every person got removed from Facebook–some bad actors just keep coming back at massive rates, and we have the solution to prevent these large-scale attacks.
Q. What’s your pricing schedule?
In the United States, this is only about $0.01 per login. Generally, we charge a small margin on top of the cost of sending verification SMS, to cover the development, operational and server costs.
Generally, humanID will cost similar or less than implementation a SMS-based login.
Q. What if my users are international? How does this affect pricing?
The pricing schedule remains the same, but SMS rates do vary by country. Please see our website for a pricing table.
Q. Do you have a free trial?
We do offer free trials for a certain amount of user logins. Please contact us directly to discuss specifics.
Q. Are you GDPR and CCPA compliant?
Yes! humanID is compliant, and even better, it enables clients to be compliant without any efforts. humanID does not send the client any PII (personal identifiable information), as irreversible hashes do not fall under that category. So as long as the client does not collect other PII, it removes the legal efforts and review required to ensure compliance with the new legislation.
Q. Are you HIPAA compliant?
Yes. Neither do we save any ““Protected Health Information” or other user data, nor do we provide any to the platforms we’re working to. Of course, there are other, partner-side requirements that websites have to fulfill to offer a HIPAA compliant product, but humanID does not stand in the way of this!
Q. Why is humanID the future for App businesses
When apps use the single sign ons offered by Facebook or Google, they often become uncomfortably attached to them. 60% of small businesses that have data leak go bankrupt. Data leaks cost a company an average of $8.13 million. Companies, especially young ones, underestimate the risk of integrating with Facebook or Google.
humanID protects companies from these risks because it does not collect any Personally Identifying Information, or PII. Companies using humanID are immediately compliant with new privacy legislation in California and the EU, a sign of the long term viability of humanID as more states and countries move towards similar legislation.
 humanID CAPTCHA works with existing sign-on services. Users faced with the humanID CAPTCHA send their phone number to humanID (and only humanID). humanID sends an SMS code to this number, verifies that the human has entered the correct code, and deletes the phone number. humanID then tells the website that the user is human, and sign-on is complete! As a trusted 3rd party, humanID lets websites verify the humanity of their users through phone numbers without jeopardizing their privacy. Either way, privacy is ensured and abusive behavior managed!
humanID CAPTCHA works with existing sign-on services. Users faced with the humanID CAPTCHA send their phone number to humanID (and only humanID). humanID sends an SMS code to this number, verifies that the human has entered the correct code, and deletes the phone number. humanID then tells the website that the user is human, and sign-on is complete! As a trusted 3rd party, humanID lets websites verify the humanity of their users through phone numbers without jeopardizing their privacy. Either way, privacy is ensured and abusive behavior managed!Q. How does it really work?
For full technical specifications, check out our whitepaper hereQ. How do botnetworks work, and how can humanID block them?
A bot network is a series of connected machines (computers) that collectively do a single task. Common applications for botnets are things like generating fake internet traffic for some sort of gain (i.e. financial), spamming many users, using your machine’s computational power for Distributed Denial of Service (DDoS) attacks. humanID requires a user to be authenticated before participating in an online transaction between machines. By requiring a SMS OTP for a user to be authenticated, and limiting the number of accounts related to a phone number, we limit the number of possible bots.Q. What is on the product roadmap beyond SSO?
Beyond our current MVP, we are projected to add an email recovery step. In addition to that, an internal organizational console to track clients and their usage, a fingerprint login, and expand the number of Software Development Kits (SDKs) to different languages to support more clients.Q. What is humanID’s tech stack?
humanID uses a variety of tech stacks across all its products and websites. For example, the Developer Console is built with NGINX/GUnicorn, MySQL, Django/Python, and HTML/JavaScript/jQuery, while our main website uses WordPress. Our iOS SDK is built with Swift and Ruby, our Android SDK with Java/Kotlin, and the humanID core with JavaScript.Q. Is humanID on the blockchain?
Currently humanID is not on blockchain.com.Q. Which open source license is humanID under, and why?
humanID is licensed under a GNU General Public License v3.0. We gave it this license to enable anybody to use, share, add features, and view the code.Q. Is humanID considered two-factor-authentication (2FA)?
Mostly yes, but it depends: If a user’s phone is password/PIN protected, as most are, a user needs to know the PIN to their phone, their phone number, and have access to their phone device. It is therefore 2FA. Having said that, on a phone without PIN access, the “Something you know” is rather weak, since phone numbers are oftentimes public knowledge, and can be retrieved from the phone device. We therefore strongly recommend users to use PIN, and we also plan, as a future feature, to enable apps to enforce a biometric or PIN-based login for returning users.Q. What if someone changes their phone number? Do they lose access to their humanID-associated accounts?
Currently, yes, but a recovery email system is in development to protect against this situation. If a user changes phones or providers without changing their number, it does not affect the humanID process at all, besides forcing users to re-authenticate with apps on their phones.Q. What hashing algorithm is used?
HumanID uses SHA-256, the industry standard and one of the most secure algorithms available.Q. Is humanID vulnerable to SIM jacking? If so, are there any mitigations?
SIM jacking is a vulnerability, but it is a non-scalable vulnerability that Google and Facebook’s SSOs also have. In addition, humanID is less vulnerable than either, because humanID does not share or store a user’s unencrypted phone number. Therefore, the attacker would have to already know a client’s phone number to perform an attack, making the vulnerability not cost effective to attack. humanID’s anonymity will limit the leaking of phone numbers drastically – and thereby reduce the targets of SIM swapping. SIM swappers oftentimes find their phone numbers and relevant personal information on the dark web, as user profiles are created based on data from different sources. humanID doesn’t track personalized information and makes it impossible to match profiles between services, even if leaks still happen. So indirectly, humanID does help against SIM swapping!Q. Can I create additional accounts with virtual phone numbers and Google Voice numbers?
Generally yes, but it is a myth that it is easy to obtain a large number of those numbers at ease and cheaply. When acquiring more than 2-3, the cost will soon reach the cost of retaining a normal phone plan. We also add additional measures to make it less convenient to maintain several accounts. Ultimately, our current situation does not entirely reach our vision of one ID per person – but it makes it near impossible and extremely expensive to build bot networks, and creates high barriers for unsophisticated users to get a second and third accounts.Q. Ok, I understand how phone-number authentication improves user accountability and privacy. Do you have any additional measures?
We deploy sophisticated limitation on the use of one device for multiple accounts, as well as some other limitations. We do not encrypt a numbers country code, thereby enabling platforms to monitor traffic for inauthentic behaviour, which traditionally originates from a small set of countries. For the future, we plan additional measures, such as helping clients monitor the relationship between accounts for inauthentic network structures, or enabling clients to allow users to anonymously verify a ‘membership number’ or external identifiers.Q. How long would it take to implement?
Implementing and using humanID is as convenient as the Facebook login, without any of the downsides. — Very quick implementation, a good developer can do it in days. The exact duration depends on the current state of your product and database structure. Our world class developers are happy to assist.Q. What if a user changes their phone number and it’s reassigned? Does someone else get access to all their accounts?
Though a user’s humanID account is linked to their phone number, a user in this situation would not have to worry about the new owner of their old number getting access to their accounts. A phone number takes 90 days to be reassigned, and humanID accounts are deactivated after 90 days of inactivity. A recovery email system is in development in case of an accidental deactivation.Q. Does humanID allow a user to use their accounts on multiple devices?
Absolutely. If a user logs in using a computer (or other device), humanID still sends the verification to the phone number linked to their account. So as long as the user has the associated device handy, logging in on multiple devices is easy.Q. Does humanID allow multiple accounts on one device?
No, because only allowing one account per SMS-associated device increases the cost of bot networks and allows our clients to more easily permanently ban bots and abusive users.Q. Is hash collision possible?
Technically, but since the probability of it happening is 4.3*10^(-60), it is an accepted risk.Q. How does humanID handle logging out?
HumanID does not mediate the logout process, nor are we even notified upon a user’s logout. The client assumes full responsibility over logout mediation.Q. Would the user have to verify using one time password every time they open an app or only upon initial login?
Depends on the implementation. It’s totally up to the client. For example, in low-security cases, such as most mobile apps, it might be beneficial for the company to only require an initial log in. However, for high-security use cases, other implementations could be done. In addition, a client could implement additional authentication on top of humanID, such as biometric or PIN-based login.Q. Does humanID ban users?
No, we do not issue general bans on phone numbers. If a client wishes to ban a user from their site, that is done entirely without notifying us. The user would still be able to log into the website using their humanID, then would be prohibited by the client from accessing their account upon login.Q. What sets us apart from a normal SMS identification?
humanID is anonymous and does not collect phone numbers.Q. Do we have the capability to enable one phone number to create accounts for a particular site that is interested in having some automation?
The site can enable that. This way, the site would know which accounts belong to the same human.Q. Can the SHA512 hashes be decrypted by brute force?
Only if someone were to first gain access to our salts.Q. What happens if DB gets leaked?
No PII would be leaked. We would have to reset all keys, which would likely force us to reauthenticate all users. If the independent database of salts is also leaked, and teh attacked has the computing power to conduct a brute force attack, PII could get leaked. Hackers would still have to hack our client’s DBs to access additional data, such as what users did on certain platforms. In the meantime, assuming we know of the intrusion, we could reset all hashes. Accessing user accounts on client sides would still be near-impossible, in particular at scale.Q. Is the login at risk of crashing due to website traffic?
No, the login can stay online independent of the website.Q. If hackers get hashes, are those good enough as logins for the site?
No.Q. Is phone number verification as secure as two factor.
Not quite, but it is a tradeoff made to support convenience and the possibility of widespread adoption. And, humanID will offer add-on privacy options for sites that require higher security.Q. Is it a drawback that users have to complain to humanID when problems arise? How can sites trust that we will provide good customer service?
Neither can you with Facebook Login, or common login services such as Firebase.Q. Is phone number verification as secure as two factor.
Not quite, but it is a tradeoff made to support convenience and the possibility of widespread adoption. And, humanID will offer add-on privacy options for sites that require higher security.Q. Are corrupt international telecom providers a risk? E.g. Russia could easily get phone numbers from its national telecom provider
Yes. This is one of the reasons we do not encrypt country codes, so we can spot a potential abuse, in particular when affecting a foreign platform (e.g. petition site, polling site).Q. What happens if I don’t have access to my phone?
If the user doesn’t have access to their phone (or to their messages via a browser etc), they could not log in using humanID. The phone access is a key element of protecting platforms from automated and artificial users. Users could likely continue using products they are already logged into, depending on the partner’s security settings. Compare to how the WhatsApp app requires a phone verification at first login, but can be used freely afterwards.Q. Why are accountability and privacy the two ingredients for a better internet?
The social internet has not been good for democratic communication. Or at least, it could do better. But why? Bot manipulation? Echo chambers? Toxic algorithms? Authoritarian snooping? Anonymity? Bad websites pretending to be good? Worse journalism? humanID answered this question by looking at the real world, and noticed two missing ingredients: 1) An anonymous identity online. It’s almost impossible to maintain your privacy online. Most of the time we’re on the internet, we use an identity – an account. We login with Gmail or with Facebook. As soon as we do, we connect our real identities to our online ones. Our governments, as they do in authoritarian regimes worldwide, can watch us online. This all but scraps the internet’s ability to guarantee free speech online. Authoritarian governments send people to jail every day for what they say online. The internet panopticon is democracy’s worst nightmare. 2) But one identity per human: The innovation of humanID is that it solves the internet’s privacy problem without exacerbating the internet’s accountability problem. We’ve grown up with an internet that’s taught us to expect junk: from the mysterious trolls who seem to have infiltrated comment sections on every corner of the internet, to the keyboard warriors that every town Facebook group has, to the bot networks flooding social media sites with fake news, the social internet just isn’t something we take seriously as a forum for discussion. But this is so sad! The thought of having thought provoking public discussions online seems so imaginative that we forget that this was exactly what the internet first started as, and what it could be! Either as a login or a CAPTCHA tool, humanID helps make online identities that are private but restricted to one identity per human. humanID’s login is completely anonymous: you give us your phone number, we use it to create your secure online identity, and we throw away your phone number. (Anonymity). Meanwhile, humanID login and CAPTCHA require a phone number for new accounts, significantly increasing the cost of developing online bot networks and making it easier for communities to hold human users accountable on their sites. (Accountability).Q. What’s the future humanID imagines?
With a healthy balance of anonymity and accountability online, the humanID internet resembles the real world. Private People speak their mind in the real world because they can know and manage exactly who’s watching. The government can’t listen and imprison you. Your job can’t listen and fire you. Your entire community can’t indiscriminately listen and cancel you. humanID mimics this online. You retain full control over your online identity. And your actions in separate communities are isolated from each other – just like your close friends don’t tell your boss what you’re doing off-work. No trolls In real life, you get kicked out of establishments and social groups when you misbehave. You can’t put on a mask and keep trolling the same establishments and social groups, so people don’t. humanID brings accountability to the online world. On the humanID internet, trolls are either easily banned or decide for themselves to behave. Imagine that: an internet that self regulates civility. Real people And what about automated accounts? There aren’t bot networks in the real world because robots can’t impersonate humans cheaply. humanID reduces the accounts that can be made per dollar spent by 97%. Gone would be the fake accounts flooding Twitter with spam and fake news. We’d learn to treat our online identities with the same respect we do our offline ones. We’d expect a real person on the other end of every online interaction. We’d expect a civil person at the other end of every online interaction. Imagine the possibilities for democracy! humanID doesn’t stop at mimicking the real world online. humanID powers the internet to go beyond. The internet has incredible potential for democracy. Internet identities are more egalitarian and accessible, with less discrimination on basis of class, gender, race, social status. Power has a harder time concentrating in the hands of a few if everyone would share an equal voice. It’s a tool for grassroots movements to organize. It can be used to fight authoritarianism as it did in Hong Kong. It’s more innovative. But a lot of businesses can’t be built right now. There is not enough trust, and too much spam. humanID unlocks the potential of these ideas, like a humanID partner app called Polarizer that offers people a space to specifically seek out and engage with opposite viewpoints, or a humanID partner group that gives transgender people a truly private online community. The internet is humanity’s great new asset. It lets us connect with each other like never before. At humanID, we hope that by adding the right rules we will make this communication altogether great for society.Q. Isn’t anonymity incompatible with accountability?
Our tech is the solution to that exact dilemma. Anonymity is bad because typically it guarantees no consequences – you can just rejoin under a different identity. With humanID, you can’t. Think about voting – it’s anonymous, but everyone can only vote once. Both of these things need to be true for democracy to work!Q. Are other things to blame for the crisis of misinformation?
Nothing solves the problem completely, but we think humanID attacks the core of the problem. It isn’t a coincidence that the rise of misinformation has coincided with the rise of the social internet. The partisanship of cable media must be understood alongside the internet phenomena that influences the cable media companies. Often the direction of this street is from the internet to cable media. QAnon starts on 4chan message boards and ends up on Watters World. Internet trolling and fake news enrage citizens, so Fox and MSNBC business managers push their programs to stoke this anger and increase viewership. Democracy generally works. The internet has destabilized democracies because it’s opened up a new social world without the traditional rules and safeguards against abuse. humanID’s mission is to tinker with the structure of the internet in a way that lets democracy — for all tis imperfections — flourish. The threat of automated propaganda efforts online is severely understated as well, and may force actions like humanID even faster.Q. Does this create new problems that we’re not thinking of?
The security risks are lower than for a FB login, but higher than a fully decentralized solution. We could get hacked – though it’s much less likely than other sign-ins, and likely easier to mitigate the effects. A country’s telco could block us if the government doesn’t like us – but would come indiscriminate for all humanID services. If we’re big already, that could mean inability for the country’s citizens to use all humanID services. We’re a US-incorporated foundation, which some European activists consider risky, due to access of US intelligence services and ability to force companies to clandestine collaborations. Future product improvements will try to diversity/decentralize legal setup to take advantage of stricter privacy laws in other countries.Q. What are examples of sites that restrict users to one identity, and how has that worked out for them?
From worst to best on this metric alone(!): 1. Communities that offer email login 2. Communities that offer FB & Google login 3. Communities that only allow phone-number based logins a. E.g. most dating sites. Signal. WhatsApp 4. Sites that require payment (e.g. e-commerce companies). The healthiest parts of the internet are 3 and 4.Q. What issues have particularly suffered from fake news / the lack of humanID?
Here’s one example: the New York attorney general’s office revealed that the FCC’s watershed 2017 net neutrality rollback was unduly influenced by millions of fake comments from major broadband companies on one sidem, and a 19 year old college student on the other.Q. Why should people assume humanID is trustworthy?
We are a nonprofit. We do not have fiduciary duty. We are open source and transparent. Anyone can verify our code does what it says.Q. Is there a concern over giving anonymity to potentially dangerous extremists?
In a perfectly traceable internet, we have to make a decision to either let governments track everything, or accept a certain risk. There is no compromise between them. And anonymity gets lost as soon as users buy something. Who does more harm right now, and is the worse danger, anonymous extremists with their words, or authoritarian governments imprisoning millions for their words and thoughts?Q. What is the extent of the bot problem for fake news?
The impact is hard to measure because network dynamics are complex. But bots are often the first to repost fake news links on Twitter, often in a matter of seconds, suggesting that they may launch the fake news cascades which may later be propagated by regular humans. Media manipulation with bots — “computational propaganda” — is also in its infancy. Future efforts will be significantly more sophisticated and impactful.Q. Why isn’t content moderation the solution?
It’s expensive, and it relies on our trust in tech companies. But also, bots can beat content moderators:
Q. Facebook is non-anonymous but still seems problematic. Does that mean your solution won’t solve us much as it claims?
The Facebook ecosystem is not a one-human, one-identity site, although many humans use it that way. A significant share of Facebook accounts are fake — it takes down close to a billion fake accounts each quarter. Accounts like this, and troll accounts, have amplified fake news stories and normalized the type of toxic behavior Facebook struggles with.Q: Why is privacy important?
“Arguing that you don’t care about the right to privacy because you have nothing to hide is no different than saying you don’t care about free speech because you have nothing to say.” – Edward Snowden You don’t need privacy until you do.Q. Who are humanID’s competitors + What sets aside humanID from its competitors?
(1) Facebook, Google, Apple & other SSOs Big Tech companies have suffered from trust and privacy concerns and do not provide protection from breaches nor blocking blots and abusive users. Apple has recently introduced “Sign In with Apple”, which is a step into the right direction, but 85% of global internet users don’t possess an iPhone. In addition, for-profit organizations, like Apple, Facebook, and Google, have incentives to misuse user data to benefit their businesses and have proven to do so consistently. (2) Email-based Logins Email based logins are prone to hacks and leaks and are not user-friendly due to the required application switch. In addition, they do not block fake accounts and trolls, as creating an unlimited number of new email addresses is easy. Email based logins also do not provide protection from breaches or block blots and abusive users. Newer solutions, such as fast.co, add a fancy “magic link” functionality. But they suffer from the same downsides and therefore lack sufficient differentiation, which is why they struggle to even gain the level of adoption humanID achieved with at almost zero cost. (3) One-Time-Password logins SMS logins are generally faster and easier, which is why the market trends this way. But skepticism remains for users in the age of robocalls and spam SMS. OTP platforms and logins such as YC-backed cotter.app offer convenience and better protection against fake users than email, but lack the additional limitation that humanID enforces, not to mention the privacy protection. (4) Other blockchain-based identity efforts In recent years, a long list of blockchain-based identity providers have been founded. The large majority of those platforms aim to replace the customer KYC (Know-Your-Customer) process. Although we share many of the same goals as these organizations, we are more likely to be adopted by the a mass market as these platforms require cumbersome user onboarding processes, for both users and platforms. (5) Government identities The largest and potential most dangerous player in the identity space is the government. Many governments are now realizing that the only way to govern and control their population is to connect online identity to physical citizens. For example, India is building Aadhaar, connecting an online identity to biometric information. Many countries are thinking along similar lines, if not already doing so in the example of China. This builds an infrastructure that possibly enables dystopian, irreversible surveillance at a scale. Our time is quickly running out to defeat such a scenario. Compared to the leading online identity providers such as Facebook, Google and OTP solutions, and startups such as Sovrin, Civic or SOLID, humanID differentiates in our product design, extreme ease-of-use and nonprofit legal structure: 1. Designed to fight bots humanID is the first identity solution that uses phone numbers (and to a certain degree devices) as a limiting, “real-world” factor to discipline the number of accounts to sign on as authentic users. This is a true game-changer because it significantly increases the cost of bot deployment to spread fake news, spam, and online bullies. Our product design is deeply rooted in our belief that a lack of accountability is the driving force behind toxic Internet culture and the spread of fake news – a causation confirmed by studies and experts. 2. Ease of adoption humanID is designed for mass adoption. Thanks to minimal data requirements, and easy, cross-platform login, users can sign-up within seconds. Contrary to similar providers, humanID doesn’t require customers to download a new application. Similarly, we are creating maximum simplicity for developers in terms of implementation and testing. humanID’s SKD is modeled after the Facebook Login SDK. Developers only need to spend a few hours to add the humanID button onto their existing login flow. There’s no requirement to host nodes, nor is there need to change existing database structure. The humanID login is automatically compliant with GDPR and the California Consumer Privacy Act. 3. Nonprofit structure We perceive our nonprofit structure as a core advantage. We value full transparency, open-source principles, and complete privacy. We have neither incentives nor ability to store or sell user’s data.Thanks to our legal structure, users can trust the endurability of this vision. The Internet is built on layers upon layers of open-source, free-to-use layers and protocols – humanID is created in this tradition. humanID is a movement. Our organization is composed of 4 teams with more than 40 members from all around the world. We take pride in producing original content on privacy, cybersecurity and disinformation. Our Medium channel and podcast produce high quality content every week to educate the world on the impact of privacy breaches and coordinated inauthentic behaviour (CIB). Our ambassador program has attracted students across America, gaining momentum and onboarding advocates to adopt and spread the word of humanID.Q. Is humanID the first to use phone numbers as identity?
More and more apps – especially internationally = use the phone number as identifier, due to the increased security and comfort. But this creates new issue around privacy and spam SMS. humanID technically doesn’t use the phone number as identity – but rather a irreversible hash of the phone number, while deleting the phone number itself. This creates full anonymity, and as far as we know, we’re the only ones doing that.Q. What happens if big tech companies just do the same thing?
Then our mission will have been accomplished. But, this is unlikely anyways because only a 3rd party nonprofit can truly be trusted. And big tech companies do not have the incentive to stop collecting data. Most of Facebook and Twitter’s customers are brands and advertisers. While some of those are smart enough to optimize their marketing campaigns based on real purchases, most are not. Most advertisers just buy “views”, “eyeballs” and “clicks” for their ads. This makes bots and other accounts an important part of social media’s brand value. Facebook, for example, deletes around 2 billion (2,000,000,000) fake accounts every quarter. Nevertheless, experts estimate that 30-50% of the remaining Facebook accounts are fake. Imagine what it would do for Facebook’s market cap if they were to announce tomorrow that their user numbers decreased by 40%!Q. How will humanID further its product?
Currently, humanID’s focus is as a single sign-on option for sites. Over time, we have several long term product ideas. These include:- Collaboration with any issuer of identification (from government IDs to union membership) to verify membership in an entity anonymously
- Standalone app to manage (and potentially even monetize) your personal data and control who has access
- Anonymous email service similar to Apple ID’s emails – anonymous, unique per service, to stop spam at scale
- Replacing “Proof-of-Work” (which destroys the environment) in crypto with humanID
- Working with social network clients to add “network factors” to verify humans
- Collaboration with privacy-first browsers for more convenient login


