Can CAPTCHA Prevent DDoS Attacks?
By Caroline Wang
May 12, 2021
With the increasing reliance on the internet and technology comes the risk of malicious attacks and data breaches. While some attacks target everyday citizens and consumers, other attacks focus on information technology companies, e-commerce businesses, government agencies, and more. Obviously, there have been an increasing number of cybersecurity measures developed over the years in an attempt to limit such cyber attacks such as multi-factor identification and antivirus software. On the other hand, corporations and websites themselves have alternative forms of online protection against targeted attacks such as a distributed denial-of-service attack (DDoS), one of which is CAPTCHA.
What is a DDoS Attack?
A DDoS attack stands for a ‘distributed denial-of-service’ attack. These attacks exploit the capacity limits of network resources, sending numerous requests to the attacked resource. As an example, a DDoS attack on a company’s website is excessive requests to the site. If the number of requests exceeds the website’s capacity to handle multiple requests, the attack prevents the website from functioning properly and limits the number of actual consumers who are able to access the site. The two primary results of a DDoS attack are slower responses to each request or ignored requests, potentially crashing a website altogether. Such attacks can have lasting effects, keeping the website down for days or even weeks. While the quantified impact of a DDoS attack varies depending on the business or organization, businesses can lose over $20,000 an hour from an effective attack. For some IT companies, that figure ranges from $300,000 to $1,000,000 lost an hour. Thus, repairing the network in a timely manner is a high priority should a DDoS attack occur.
In order to completely overload the capacity of a network’s resource, cybercriminals enlist the help of multiple machines by creating a zombie network of devices. These infected computers, usually called a botnet, are under the direct control of the cybercriminal and contribute to the mass infestation of the network. Because the cybercriminal can control the actions of all the zombified devices, they can easily manipulate hundreds or thousands of computers to overwhelm the targeted network, effectively inciting a DDoS attack.
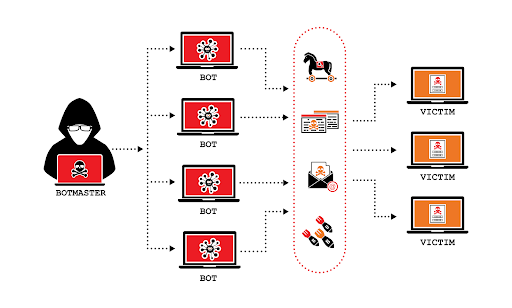
What is CAPTCHA?
CAPTCHA stands for ‘Completely Automated Public Turing test to tell Computers and Humans Apart’ and is essentially a type of challenge intended to differentiate between humans and machines. The goal of CAPTCHA puzzles is to pose an unsolvable problem to a computer but remain an easy one for the human eye. Common example puzzles include a series of disfigured letters or numbers that are unidentifiable by computers. Differentiating between humans and machines is essential to protect user privacy and to prevent bot attacks. CAPTCHA’s role in keeping the internet spam and bot-free helps ensure that everyone’s internet experience is better. Some examples of negative behavior that CAPTCHA prevents include the creation of emails for spam and the purchasing of limited-supply goods for resale at inflated prices. By preventing botnets from creating spam accounts, since the attacker’s only option would be to individually solve the CAPTCHAs on every infected device, CAPTCHA can successfully prevent a DDoS attack.
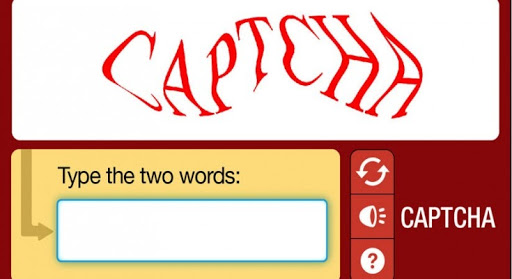
Unfortunately, while CAPTCHA has the potential to mitigate DDoS attacks, widely used CAPTCHA solutions such as Google’s reCAPTCHA have been discovered to risk user privacy. Google’s no CAPTCHA reCAPTCHA requires users to check a single box to affirm their identity. The idea behind the test is that Google tracks the cursor movement of the user as it moves to check the box, and reCAPTCHA assigns each user a score on how likely they are to be human. However, the issue with this system is that Google can collect a user’s data on every page of its website that has a reCAPTCHA logo, which is actually nearly every page of its website.
humanID provides a simple and secure alternative to regular CAPTCHAs as well as Google’s reCAPTCHA. Rather than requiring users to decode puzzles to confirm their identity or risk their information for a for-profit organization, a phone number is all humanID’s CAPTCHA solution needs. Once a user inputs their phone number for verification, humanID’s secure system will send the user a verification code. Afterward, the data is erased for optimal privacy and protection. As a nonprofit organization, humanID prioritizes providing our clients with the highest level of security and convenience, so your users won’t ever have to worry about their personal information.
What are the implications of DDoS attacks?
To fully understand the implications of a DDoS attack, we can examine an example. On October 16th, 2020, Google’s Threat Analysis Group posted a blog update indicating a measured DDoS attack launched from several Chinese internet service providers (ISPs) back in September of 2017. These attacks peaked at 2.5 TBps, where 1 TBps is equivalent to 1,000 gigabytes per second, which measures the largest recorded DDoS attack, and it took six months to fully resolve. Google reported that the attack had been state-sponsored; the government-backed group had exploited four ISPs in China to send Google flood traffic. However, despite being the largest DDoS attack recorded, company security engineer Damian Menscher wrote “the attack had no impact.”
Over two years prior, on February 28th, 2018, GitHub recorded a DDoS attack of 1.3 TBps. This attack was a memcached DDoS attack where an attacker attempts to overload a specific victim with unrequested internet traffic, overwhelming both the victim and the website itself. With a memcached DDoS attack, there is no zombie network of bots involved. Instead, the attackers leveraged the amplification effect of a caching system. Luckily for GitHub and its users, the company was using a DDoS protection service which automatically triggered mitigation of the attack only 10 minutes after its onset. The entire DDoS attack ended up only lasting around 20 minutes.
In both of these cases, the effect of the DDoS attack was minimal. However, if mitigation services were not deployed in a timely manner, both of these corporations could have suffered serious losses in visitor satisfaction. This would have caused greater implications for the companies as limitations to their services would drop their assets, harming their reputations even more. Thus, it is important to have cybersecurity measures in place to lower the chances and effectiveness of a DDoS attack.

Implementing a CAPTCHA can prevent a DDoS attack as it stops an attacker from performing database-related operations that can overload a website’s capacity. Because only legitimate users are able to pass a CAPTCHA, any attacking machines or zombified computers cannot pass this security checkpoint. Thus, CAPTCHAs can help filter disruptive traffic. However, there is one obvious caveat to the effectiveness of CAPTCHA at mitigating DDoS attacks. If a very large population of users coordinated to visit a website simultaneously on separate devices, they could each solve their respective CAPTCHAs at the site’s security checkpoint. This could potentially lead to a successful DDoS attack as an overwhelming number of coordinated requests can lead to the collapse of the website itself. Yet cases of this are largely unfeasible due to the excessive number of people and coordination involved. Thus, in theory, CAPTCHA should be an effective solution to prevent DDoS attacks.
Ultimately, data security and privacy protection services are a necessity to the success of a company’s website. Without preventative measures to differentiate bots from human users, a website remains prone to DDoS attacks that overwhelm its network’s resources. These attacks are generally harmful to both the website service and the average consumer, making it essential to implement cybersecurity measures. However, certain CAPTCHA solutions like Google’s reCAPTCHA work at the expense of user privacy which is why you should use a privacy-protecting solution like humanID.


