8 Ways to Minimize the Risk of Data Leaks
By Adrian Lăpădat
February 23, 2022
According to IBM, the average cost of a data breach is $3.86 million dollars, and it takes about 8 months to identify and contain it. Data breaches are becoming increasingly prevalent and expensive, causing issues in relation to remote work, small business operation, and more. In 2021 alone there were 1,862 data breaches, making it a record year for this type of cyber attack.
Data leaks are just as much of a concern. A data leak and a data breach are not the same thing, even though the terms are often used synonymously. A data leak is when sensitive data is unintentionally exposed either at rest or in transit. Meanwhile, a data breach is when an unauthorized party accesses or an attacker steals sensitive data.
Vulnerabilities can lead to either type of attack overlap; an IT infrastructure that is vulnerable to data leaks is likely vulnerable to data breaches as well. So when you minimize the risk of data leaks, you minimize the risk of data breaches as well. The umbrella term for the many practices that can be implemented to minimize risk in this area is called Data Loss Prevention, or DLP.
Data leaks can expose customer information, trade secrets, and precious company data. Do not leave your information in the open for attackers—here are 8 ways to minimize the risk of data leaks.
1. Locate and Protect Sensitive Data
Before you start implementing DLP, identify sensitive data. Identify which information needs the highest levels of protection, and establish appropriate protections for other information. Use this knowledge to move forward as you implement DLP through third parties, employee training, and content control. The other items on this list complement a thorough understanding of your company’s needs.
Disposing of data properly is also a part of protecting data. Improper disposal of old devices or data that is no longer necessary could mean data leaking from the company and into unscrupulous hands.
2. Evaluate Permissions
While data visibility is important, information that requires the highest degree of security should only be accessed by a limited number of trusted individuals based on their job requirements.
Ensure that confidential data is not accessible by users who do not need access to it, and critically evaluate user permissions elsewhere. It is a difficult game of finding the balance between data visibility, which may improve your business’ cohesion, and weak security, which could leave you open to data leaks.
3. Encryption
The oldest trick in the book. It is still in there because it is a really good one. Encryption keeps data confidential, so only authorized users with keys can view encrypted data. If your data does end up out in the open, encryption makes it much harder to exploit.
- Passwords, financial, and personal information should be encrypted.
- Requiring robust authentication
4. Secret Management and Protection
A secret is like a password one software uses to interact with another. This password can be used to gain access to secure resources or private data within applications, tools, the cloud, and more. Human users and software access your technology stack in three ways:
- Intentionally | Users use a secret to access your technology stack
- Accidentally | Access is misconfigured or given to people who should not have it
- Maliciously | Usually done by finding and exploiting the weakest link, which often exists due to gaps left by misconfigured access
To prevent this, monitor your code for points where secrets are used incorrectly or provide misconfigured access. A variety of tools can examine code for vulnerabilities, and you can pick the right one for your platform.
5. Monitor Network Access
Before a data breach, attackers will usually scout your network to identify vulnerabilities. By monitoring network access, you can identify suspicious activity from potential attackers and prevent it.
6. Automate Security
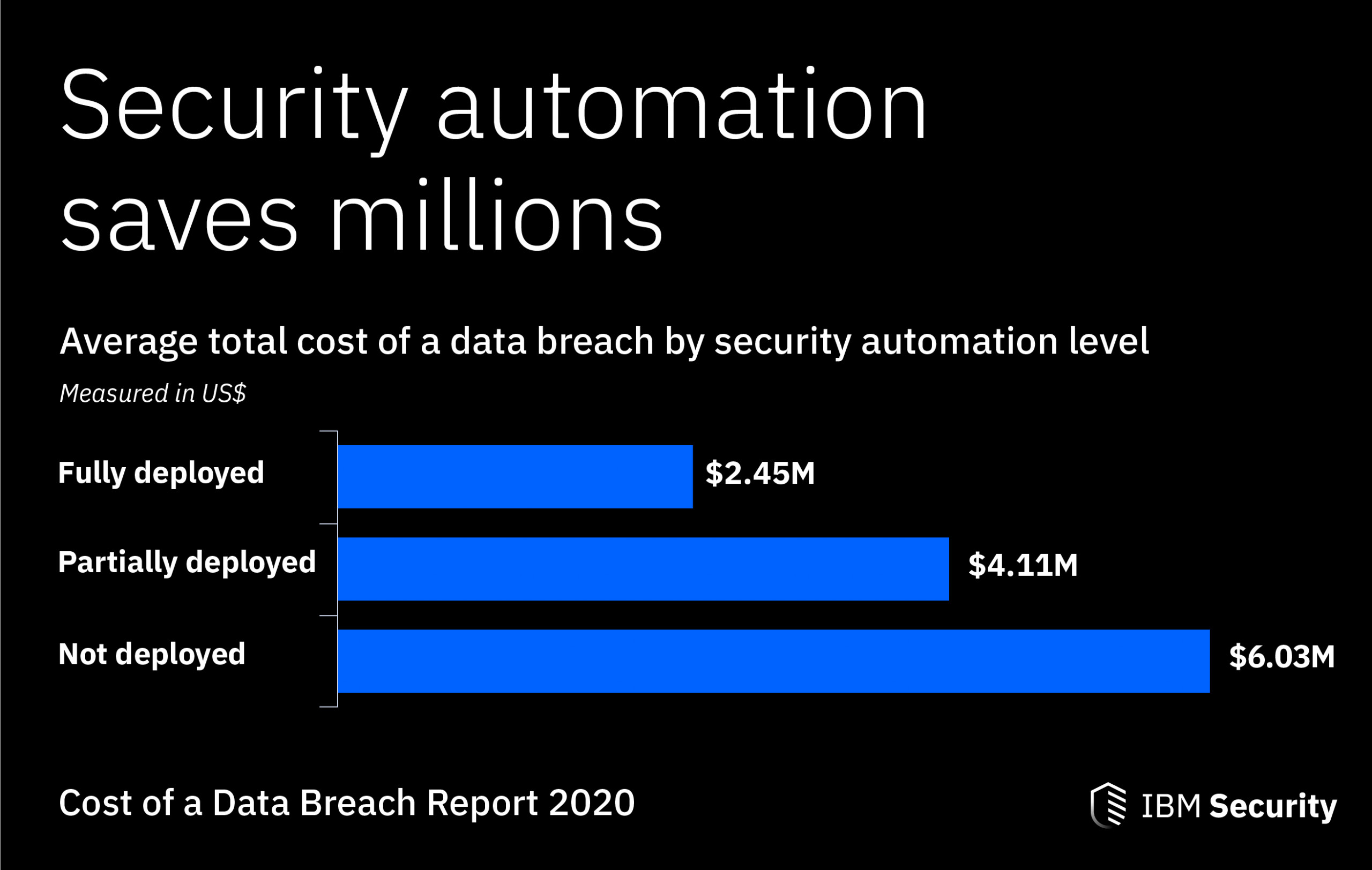
When developers, web engineers, and IT staff dedicate their time to manually assessing security, the repetitive work involved can lead to errors. Automated security lets employees focus on higher-level tasks, while helping you identify data leaks. Additionally, it can significantly reduce the average cost of a data breach.
Since automating security can seem quite intimidating, here are some resources to help.
Software Testing Help has a list of their top 11 powerful cybersecurity tools, which can help you find the right tool for automating your business’s cybersecurity.
The Open Web App Security Project (OWASP) Zed Attack Proxy (ZAP) can help automate your security, and it is free. An overview of web app building and testing with ZAP is available here in this slide deck from OWASP.
To expand on OWASP as a resource, it provides access to thorough cybersecurity knowledge and reference materials you may not be able to find elsewhere. It is an open-source nonprofit run by cybersecurity experts who share their knowledge with others, and a valuable resource for organizations looking to boost their own cybersecurity.
7. Employee Training and Content Management
85% of data breaches involve humans. Though employees may constitute a risk, they are also the most essential asset in minimizing the risk of data leaks . It is a matter of consistency and developing employee habits. A business should work together with its employees to develop best practices which stem both leaks and breaches.
Another way to address the human aspect is through content management. This can include:
- Limiting access to company information outside of work devices
- Requiring robust authentication
- Ensuring that sensitive data cannot be sent outside the company
A policy that governs the use of devices, such as password complexity, download and application guidelines, and login timeouts will help prevent data leakage.
You may wish to consult the FCC’s cybersecurity guidelines for small businesses for further advice.
8. Assess the Risk and Security Capabilities of Third Parties
It is important to assess whether the security of third parties are rigorous, as they may not be as reliable as your own.
- Administer risk questionnaires using questions from security frameworks
- Use a third-party that specializes in cybersecurity to assess these other third parties
- Conduct risk compliance to assure partners comply with PCI-DSS, GDPR (European Union) and CCPA (United States), and HIPAA, as well as voluntary standards like SOC-2.
humanID is an example of a secure third-party. We implement anonymous two-factor authentication (2FA), which helps prevent data leaks and breaches. Once a user initially logs in with their phone number, this is tied to a slow salted hash and the phone number is then deleted. We store that hash in our database to confirm user authentication for future access, though this hash is never traced back to the user’s phone number. Our login data is stored in a hash instead of encrypted, making it extremely secure. And because we store a hash instead of the phone number, login with humanID is anonymous.
With humanID, you can minimize the risk of data leaks because all of our login data is encrypted, plus we immediately delete phone numbers after validating login. In addition, the identity of a user on one application is unique, so if another application compromises their humanID-tied user identity, it will not affect all of your applications.



Thanks a lot for sharing this with all of us you actually know what you’re talking about! Bookmarked. Kindly also visit my website =). We could have a link exchange contract between us!