Defining IAM and IGA
What are they and why does it matter?
By Christopher Fryzel
April 21, 2021
IAM and IGA are two of the most common methods for identity management, and it is important for enterprise users to understand the purposes and functions of each system, as well as the benefits and limitations.
What is Identity and Access Management (IAM)?
Identity management, or identity and access management (IAM), encompasses verifying a user’s identity and their corresponding level of access to a system. In this case, users are customers that utilize the front-end of the system and employees that improve the back-end. IAM establishes one digital identity for each individual user, therefore simplifying the maintenance, modification, and monitoring of each user’s access. Thus, IAM gives administrators the ability to change users’ roles, track their activities, create activity reports, and enforce policies without interruption. Such capabilities allow the administration of user access throughout an entire business. Some tools that IAM provides include API security, identity as a service (IDaaS), identity analytics (IA), and risk-based authentication (RBA). API security makes IAM useful for B2B commerce, and it makes cloud integration seamless by ensuring safe transactions between software tools and interfaces. API security is also used to secure single sign-ons (SSOs), such as humanID. IDaaS similarly allows SSO usage but through a software-as-a-service (SaaS) solution. IA, meanwhile, identifies risky behavior with algorithms and machine learning, such as with Gurucul’s privileged access intelligence tool. RBA solutions make authentication more or less simple depending on the user. For example, a low-risk user only requires single-factor authentication, whereas a high-risk user signs on with two-factor authentication when using an IAM system with an RBA tool.
What is Identity Governance and Administration (IGA)?
Identity governance and administration goes beyond IAM and supports auditing and meeting compliance requirements. While IGA still provides tools for identity life-cycle management, it also addresses analytics, logging, and reporting.
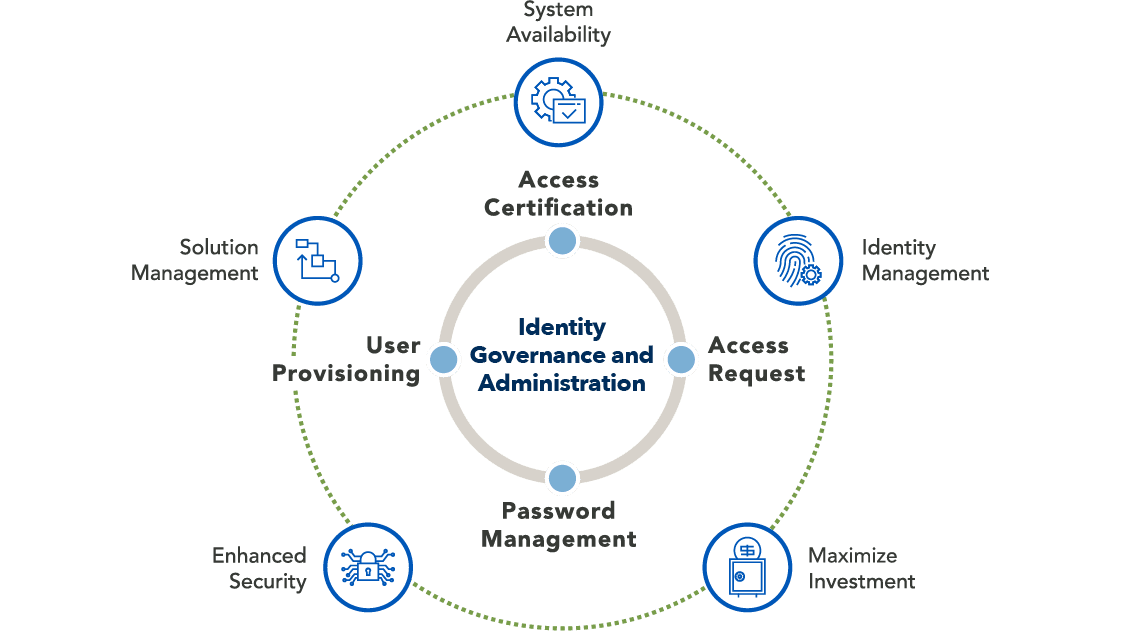
What is does IGA Do?
IGA provides automated methods for creating and managing user roles, user access rights within organizations, and user accounts. With such a system, organizations gain access to a streamlined and secure approach for user life-cycle management, compliance and governance, and risk insight. Furthermore, identity governance improves organizational security, lowers identity risk, boosts compliance with government regulations and industry standards, and heightens operational efficiencies. Some solutions IGA systems offer for identity administration include password management and access request management; these tools allow administrators to implement SSOs and streamline the process of requesting and receiving access to applications, respectively. Additionally, IGA solutions work with IAM tools to improve an organization’s scalability through centralized identity management policies, which is when identity management can occur in a single environment. Companies such as SAP provide IGA tools with centralized IAM policies. Corporations that use SAP Access Control include Mondelez International, 3M, and Stanley Black & Decker. Overall, these solutions can enhance how a company manages user identities.
How do IAM and IGA Differ?
While IGA and IAM are similar in that they seek to manage identity and access control, the function and purpose of the two differ. IAM is broadly defined, as it is any software that manages access to systems. In contrast, IGA allows organizations to connect IAM functions to meet audit and compliance requirements in addition to define and enforce IAM policy. For example, IGA might control what you can do within an application and which users can access or edit it. IGA’s purpose is to ensure that IAM policies are enforced and connected, as well as secure. Additionally, compliance professionals use IGA to closely watch which systems allow which employees and to ensure employees who leave the company lose access to said systems. Meanwhile, in this example, IAM professionals would be limited to monitoring user identification, authorization, verification, and session management.
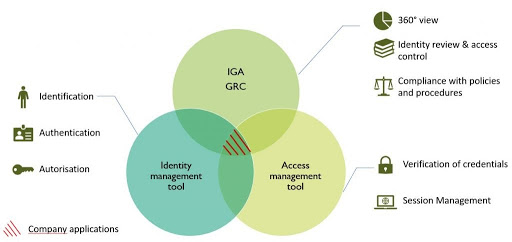
What Security and Compliance Issues does IGA Address?
Ultimately, IGA enhances security by reducing the risk of compromised identities and various violations, including policy and access violations. IGA does so by preventing weak identities from existing, monitoring identities that are potentially stolen, and subsequently removing them from the system. Moreover, IGA detects violations such as policy violations, unauthorized access, and weak controls. IGA remedies compliance and auditing issues by verifying regulations such as HIPAA, SOX, and GDPR. Thus, identity governance solutions identify and remediate the previous risk factors, as well as improving compliance with government and industry rules. IGA accomplishes this with an overarching policy, role, and risk model that provides simplified reviewing, requesting, and approving of access.
Overall, IAM and IGA both enhance enterprise security but with differing purposes and functions. IAM focuses on user identity management and access control in a much more broad sense, as IGA incorporates the regulatory and compliance aspects of governance and administration with IAM tools.


