Captcha Alternatives for Mobile Apps
By Darya Daneshmand
October 13, 2021
Are you a bot or a human user? It is essential that applications know the answer to this question to keep out ill-intentioned users, scammers, and bots. Failing to do so could result in fraudulent activity, scans of software vulnerabilities and malicious attacks. Thus, finding alternatives to CAPTCHA for mobile apps is vital for developers seeking solutions that do not present their own problems.
More mobile app breaches and data leaks were recorded in 2020 than the previous year, and increasingly sophisticated malware necessitates better security measures without compromising accessibility and ease of use. Short for “Completely Automated Public Turing test to tell Computers and Humans Apart,” CAPTCHA requires users to verify that they are a person by completing a test, typically text-based, image-based, or audio-based. The first iteration of this technology was introduced in 2000, and is still used today, albeit far less frequently. The term is an umbrella for CAPTCHA and reCAPTCHA, both of which pose significant risks to app users and developers.
Problems with CAPTCHA
User Experience & Conversion Rates
CAPTCHA puzzles are frustrating to solve and diminish the user experience (UX), especially if poorly implemented. Workflow is disrupted by the hassle of bypassing the puzzle, which can disincentivize users from continuing to utilize the application. This means trouble for conversion rates and sales. The root of the issue with CAPTCHA’s UX is that a burden is placed on users, since they are presumed guilty until proven otherwise. A number of gamified CAPTCHA puzzles aim to eliminate nuisances for improved UX, but fall short in that they still interrupt workflow.
Accessibility
As annoying as CAPTCHA can be for the average user, its use is all the more aggravating for those with learning disabilities. Blurred and distorted text-based CAPTCHAs are difficult and sometimes impossible to decipher for those with impaired vision or dyslexia, as well as older users. Audio-based CAPTCHAs are similarly problematic, failing to account for the hearing impaired. The use of Latin letters, which are most commonly used, results in increased difficulty for people whose native language is not written in Latin letters. Here’s a finding on solving time for native vs. non-native speakers from a 2010 study.
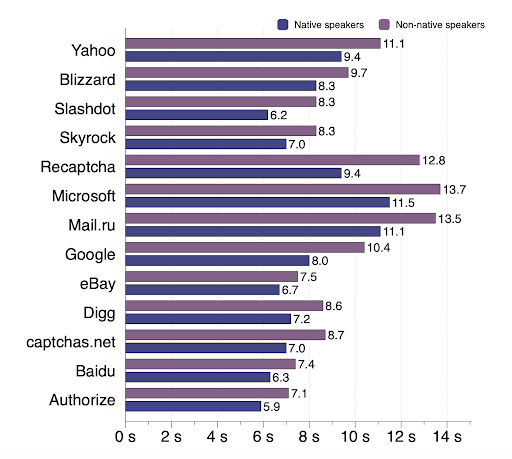
Ineffective
Aside from the difficulty of solving CAPTCHA systems and puzzles, research on deep learning techniques has found that AI can now solve these text problems with ease. And countless other studies present similar findings across other methodologies and CAPTCHA iterations. This is no little known fact; Lancaster University’s playfully alluded to this with their paper on generative adversarial networks, titled “Yet Another CAPTCHA Solver.”

Image by Darya Daneshmand
Best CAPTCHA Alternatives
Honeypots
Unlike CAPTCHA, honeypots construct traps made to detect bots that are not visible to real users. The idea is that honeypots mimic legitimate computer systems, but appeal to bots in that they have built-in vulnerabilities. Rather than addressing specific attacks like firewalls and antivirus, a honeypot such as Imperva is used primarily as an informative tool to provide you with information on existing and emerging threats. The trap consists of data that detects unauthorized use of the system, baiting bots for analysis and improvement of system security. A decoy of a set of honeypots, called a honeynet, uses a honeywall that monitors incoming and outgoing traffic with injected vulnerabilities. Options for honeypots include ones of low-interaction or high-interaction, none of which lessen user accessibility and experience in any way.
Robust user authentication & OTPs
A one-time-password (OTP) fortifies an application’s security by other means. Two-factor authentication (2FA) or multi-factor authentication (MFA) also make great additions to the strength of user authentication.
Consider using an anonymous login like humanID to ensure that bots and attackers do not breach your system. humanID’s authentication method provides both security and privacy by creating an irreversible hash (given by a hash function) that does not store or share your phone number or other personal information, simultaneously preventing password fatigue. Anonymous login offers strong authentication and security, minus the risk to personal information of users. The reason for this? User data cannot be stolen since deletion from servers occurs within seconds and does not transfer to platforms. Take this cooking analogy: CAPTCHA could be compared to a leaky sieve, where bots may fall through the cracks, while humanID’s anonymous login technology functions as a blender, shredding information that could be used to identify, exploit, and link the individual components (you) to your smoothie (that’s us!). Even if we’re hacked, your personal information remains free of risk.
Hardening the OS
Methods such as encryption and tokenization harden your mobile application’s operating system (OS) and obfuscate sensitive data. Tokenization does so by replacing data values with symbols (tokens) that cannot be understood unless an attacker has the code for it, while encryption scrambles data to keep it solely accessible to authorized users. It should be noted that hardening the operating system constitutes a useful addition to app security rather than a replacement tasked with the same objective as CAPTCHA, since it prevents bots not from breaching but from understanding and utilizing the content they access.
Tailored AI Security Systems & Timestamps
Humans and bots differ in that they complete tasks at very different speeds. Bots can achieve their objectives instantly, while real users are bound to show variability in their activity, reading fields and thinking before interacting. Sophisticated AI and deep learning systems often incorporate timestamps, which encode information indicating the time an action was performed, in their threat evaluations. Such systems employ many other metrics in their detection of “red flags,” and an understanding of their inner workings in lieu of blind credence proves a valuable asset. Timestamps are just one straightforward example. This should not be used as a stand-in for CAPTCHA and should not be heavily relied on (of course, level of reliance depends heavily on the selected software), but is a useful addition. It is also important to note that many bots preempt metrics/logs; for instance, by being programmed to take more time responding to forms to evade detection by timestamps.
Other Considerations
Mobile Device Management & App Wrapping – Pros & Cons
App wrapping describes a security practice that segments your mobile app from the rest of the device, and it is an option provided by those using a mobile device management (MDM) provider like Miradore or Hexnode. Although there are no necessary changes to the application’s functioning or UX, there are both pros and cons to its use. Use of MDM places a burden on resources such as data storage that can slow performance and worsen the end-user experience, and although it provides certain forms of protection, it does not prevent data from being breached or exposed.
How Secure is Fingerprinting Authentication?
Full fingerprints are difficult to falsify, although biometric authentication does have its flaws. The method is not foolproof, and recent research has pointed to vulnerabilities, suggesting that fake prints created digitally using common features can successfully trick mobile devices. These researchers composed prints called “MasterPrints” that were able to match true human prints similar to those of users up to 65% of the time. The technology can work in conjunction with other security features, and proves useful in that users are highly incentivized to turn on security features if they have the option of using it, while entering a password each time they enter an application can feel burdensome in comparison. Despite the miraculous level of convenience touchID provides, those implementing it should proceed with caution. Given that touchID is often used to enter apps with highly sensitive data, this is no small matter.
Key Takeaways
The gravity of this issue and the necessity of effectively securing your mobile application cannot be understated. There are a number of ways to achieve the same objectives as CAPTCHA without such detriment to users, and while this primer may impart helpful insights, we hope that it also imparts a key message: comprehensive research on the technologies that contribute to airtight systems is a prerequisite to success. A brief checklist to keep in mind when reviewing your options:
- Low latency, real-time detection
- Signatureless detection that can recognize new risks, not just previously defined ones
- Predictive detection & use of your application’s distinct risk profile
- No false-positives & transparency to visitors
It can be quite helpful to try to think like a hacker when developing your application. Doing so, and assessing ample research and advice, can save an enormous amount of grief and loss, whether that be technical, financial, or time-related. Protecting yourself makes all the difference.


