humanID Blog
What are CSRF attacks and how do we stop them?
Dreaded by companies and customers alike, Cross-Site Request Forgery (CSRF) attacks violate user privacy and generate distrust. Companies unaware of or unable to prevent CSRF attacks will not only fail to protect their clients but also receive damage to their reputations.
4 Alternatives to Passwords
Chances are you’ve had to log into a password-protected account or device within the past couple days. Whether it’s an email account or your phone, you probably find yourself entering a predetermined, secret password quite often.
How to Prevent Spam Messages
Nowadays, it seems like spam messages are an unfortunate but inevitable part of our lives. According to a recent report, 5.69 billion robocalls were made in the month of February 2021 alone.
How Truly Anonymous Login Protects Users
Even though a truly anonymous authentication system conceals user data better than any other login method, traditional media and social media have been reluctant to implement it. Many users interact with and value anonymity instinctively; the calculator app on smart phones is anonymous, but it still saves the user’s data, such as the history of their calculations.
How to Protect Yourself from Data Leaks
When a customer authorizes a company to use and store their personal information, no matter how many conditions are agreed to or what kinds of promises are made, the transaction always boils down to trust.
What is Privacy-Focused Differentiation?
What do consumers value, second to their time? With proposed and adopted laws across the world coming up such as the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR), most of us wouldn’t think twice before answering privacy.
The Fight Against Bots
Since the advent of computers, we have been forced to confront the question of humanity. What distinguishes a human, and how does one recognize and deter non-humans that simulate those distinguishing factors? Today, bots make those issues increasingly prescient.
Online Data Protection for Minors
Everyone wants to feel safe about their personal information collected by data companies online, but they don’t necessarily stop to consider what is keeping their children safe in the same respect. By age 11, approximately half of all children in the United States own smartphones, and this number has only been trending upward over the past two decades.
Top Four Ways to Protect User Privacy
Hundreds of millions of emails, phone calls, app downloads, and user accounts are made each day, with the numbers only rising. With increasing news reports on data breaches, government tracking, and even personal targeted attacks, protecting user privacy has become an inevitable issue.
What is Multi-factor Authentication?
If living entirely off the grid sounds inconvenient but you are aware that data breaches and password hacks are becoming increasingly more common every year, perhaps you are in search of a high quality security system that is not overly complicated. Hacking techniques are getting better all the time, but some of the best security practices do feel unnecessarily complicated. In search of a relatively convenient authentication practice that is not overly complicated, many people and companies are turning to two-factor authentication.
Pros and Cons of Passphrase Login
Everyday, would-be and soon-to-be hackers alike are gearing up to break into the data of millions of people while cybersecurity professionals are paid to bear down on them from the other side. In this ongoing struggle between those trying to steal private information, and those whose job is to protect it, there remains one oft-overlooked, yet vulnerable gap in the armor that no amount of money can pay to fix.
Human Voices, Episode 7: Tech & Geopolitics: Why We Should Worry
Welcome back to Human Voices, HumanID’s podcast talking cybersecurity, privacy, and news in tech! This week’s focus will be on the short- and long-term impact of big tech on domestic and world politics, and how the COVID-19 pandemic and surrounding disinformation is used by authoritarian regimes to gain power.
Security Vulnerabilities of SSOs
Single Sign-On solutions, or SSOs, have become increasingly popular as a method for users to log into their favorite applications or platforms due to the convenience they afford. They spare users the arduous task of memorizing countless passwords for the growing number of applications available to them, as well as mitigate the security risk of users using the same password for all of their accounts.
Confusing Compliance: Risks of International Data Non-Compliance
As the world globalizes and digitizes, more and more companies are finding that they have customers in different countries and states, which presents the unique problem of satisfying the laws of each customer’s place of residence for setting up sign-on pages for your website.
8 Alternatives to Facebook Login
How many times have you used your Facebook account to sign into other websites and applications and felt confident about its security? Facebook is widely viewed as the largest social media communications platform. It also offers a single sign-on called “Login with Facebook” to sign up for third-party services such as Instagram and WhatsApp.
How Startups Can Mitigate Cybersecurity Risks
New tech startups are cropping up every day, leading the way with innovative technologies and beneficial applications and platforms. However, as these technologies grow, so do the methods of maliciously exploiting them, and according to this Medium article by Ryan McGheehan, startups must address and focus on security with the same intensity that they focus on growing and expanding their business.
What is Facebook Allowed To Do with Your Data?
How often do people agree to the terms and conditions of any company without reading them, and then proceed to use their online services without any knowledge of what they have agreed to? According to multiple studies and surveys conducted since 2010, more often than not, upwards of 90% of users of any given social media platform will agree to the “terms and conditions” without reading them.
Human Voices, Episode 6: Privacy and the Internet – Why the Two go Hand in Hand
Welcome back to Human Voices, humanID’s podcast talking cybersecurity, privacy, and news in tech! This week, we’re joined by Dick Hardt, an innovator and entrepreneur who’s been in the privacy space for over 15 years and has worked on projects like OAuth, and signin.org.
Human Voices, Episode 5: Legislation’s Role in Cybersecurity
This week, we are joined by Scott Watnik, and Michael Contos, two lawyers from Wilk Auslander who focus on cybersecurity and privacy. They’re here to talk with us about legislation in the cybersecurity space, and how it can affect companies, both big and small.
4 Steps to Improve Conversion Rates
For small businesses, website traffic is essential for marketing products and services to customers. The higher the number of visitors, the more opportunities a business has for growth. The NN group defines “conversion rate” as the percentage of website visitors who take a desired action.
The Risks Associated With Using Facebook Login
With over 2.7 billion monthly active users and counting, Facebook has become the go-to online social networking platform. Ever since Mark Zuckerberg launched the site in 2004, friends and family have been able to stay in touch with each other more digitally than never before. In fact, 88% of users are on the social networking site to keep in touch with loved ones. Friends and family members have instant access to each other’s life updates through news feed posts.
Alternatives to CAPTCHA
CAPTCHA, which stands for “Completely Automated Public Turing test to tell Computers and Humans Apart” is a test that is meant to differentiate real human users from bots that are using whatever services the CAPTCHA is protecting. You’ve dealt with them before. While there are a number of different CAPTCHAs that are used, the most commonly used in the current era is reCAPTCHA. And this current iteration definitely has its merits, such as ease of implementation from a trusted source, but unfortunately, the ineffectiveness of CAPTCHA is slowly becoming more and more apparent , so developers are starting to look for alternatives.
Your Site and Bot Attacks
As a web developer, your visitors and your site’s information are crucial. The last thing you want are bot attacks affecting your site traffic. A major block of internet traffic online is dedicated to bots scouring and interacting with websites and apps; approximately fifty-percent of all internet traffic comes from bots with about one-in-five website requests being generated by bad bots.
Company data security and ensuring compliance with GDPR and CCPA Requirements
Privacy protection has become not just a concern for individuals but also a major topic of discussion for governments across the globe. Two major pieces of legislation that are forcing tech companies to become more transparent and accountable in their handling of personal data are the European Union’s General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA).
An Introduction to Online Privacy
The Internet is a really fun and cool thing. But, as I’m sure you know, the Internet can also be a terrifying place. There are many entities on the Internet who want, and can, get a hold of all the juicy details of who you are. But it doesn’t have to be this way.
Holding Hospitals Hostage: An Overview of Ransomware Attacks on Hospitals and Healthcare Systems
As hospitals continue to increase their array of interconnected machines and software to care for and manage patients, they become increasingly reliant on digital ecosystems. Yet, this process of attempting to streamline and unify once separated systems is not without its dangers.
Designing Digital Identity
Personally identifiable information can be any data that helps identify a person. The more uniquely identifiable the data is, the more sensitive it is said to be. Features that are used to identify people in the real world often include our full name, date of birth, gender, residence, ZIP code etc. We are largely forthcoming with this information when asked. After all, why wouldn’t we be?
Password vulnerabilities and mitigations
Passwords are one of the most common forms of authentication in today’s very technological world, and for good reason. They are easy to set up and use, and for a lot of applications, are perfectly adequate. Unfortunately, as more and more applications require users to create accounts to utilize their full capacity, the weaknesses of passwords have begun to show themselves.
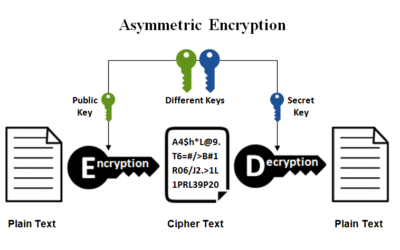
What is encryption?
Any phone call you make, text message you send, item you purchase online, or bill you pay for, uses some form of encryption to protect your identity and maintain your privacy. The roots of encryption can be traced to ancient Greece where codes, or ciphers, were used to jumble numbers and letters on paper to encode information that was transferred between generals.
Disinformation and misinformation: why the distinction matters
If you’ve been on the internet for any amount of time, you have likely seen something — be it a news article, a social media post, or whatever else — which seems sensationalized. Let’s imagine a self-described news agency that publishes an article about a presidential candidate making a policy promise, but intentionally alters what they say to such a degree that it no longer resembles the candidate’s initial statement; we’d call that fake news.
FAANGs Out: What Big Tech Wants With Your Data
Tech companies love to collect data on their users. Our personal data is a hot commodity for companies that want to optimize their services, sell something, or keep you as a returning user. With advertising being a 600 billion dollar industry, it comes as no surprise that there are many companies with a motive in utilizing personal data to try and get a profit out of you, the consumer.
Human Voices, Episode 4: Jon Callas on Entrepreneurship in Cybersecurity
This week, we have expert Jon Callas joining us and shedding light on President Trump’s TikTok ban, COVID tracking apps, and what it’s like to be an entrepreneur in the cybersecurity industry. He is a senior technology fellow at the American Civil Liberties Union. You might know him as the creator of PGP Corporation, makers of Pretty Good Privacy universal serve, The Blackphone, and an early developer of operating system software at Apple.
When are you sharing too much on social media?
Staying connected is important. In our current day and age, the internet gives us the opportunity to be more connected than ever, allowing us to communicate both actively and passively with friends and family around the globe in real time. Using social media like Facebook or Twitter, you can post updates on your life so that even without calling or texting people, they can still be informed on how you’re doing. This is a very powerful tool with a large amount of benefits, but are there risks?
Human Voices, Episode 3: Big Tech’s Control Over The Media, ft. Dipayan Ghosh
This week’s focus is on the intersection of digital media and civil rights. Dipayan Ghosh is a senior fellow at the Harvard Kennedy School and lectures at the law school. He was a technology and economics policy advisor in the Obama White House and a global and private policy strategist at Facebook, both sort of around the 2016 elections.
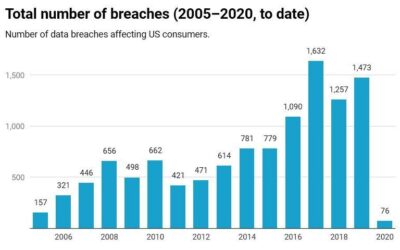
7 Social Media Sites and their Data Breaches
In a previous article, we talked about how social media companies harvest a large quantity of data from the people who use their services. Monetizing data is how sites like Twitter and Facebook make most of their income, but these services have tried to promise users that their most private and compromising data is never sold or made vulnerable. In this article, we will explore times when these social media platforms have failed to adequately secure our data.
Why is humanID Superior to Other Social Logins?
You come across a new clothing website that has some shoes you are interested in purchasing, but it requires you to sign up for an account. Not another password to remember! Thankfully, they have an option to login with Facebook. You use your account to sign up and browse through the rest of the catalog. Soon you start seeing ads for more shoes on your Facebook timeline. How did this happen? The answer lies in understanding SSOs and social logins.
Human Voices, Episode 2: Bot Networks and the Spread of Disinformation, ft. Doctor Kathleen Carley
This episode features Doctor Kathleen Carley, from the School of Computer Science within the Institute for Software Research International at Carnegie Mellon University. She is the director for the Center of Computational Analysis of Social Organizational Systems there.
Why App Security is More Important Now than Ever
What is the most important part of an application? Depending on who you ask, the answer might be different. User experience? The features? The in-app purchases? These three things share one thing in common. None of them are the correct answer.
Human Voices, Episode 1: The Impact of Big Tech, ft. Bart Decrem
On humanID’s first installment of a Human Voices, a podcast series talking all things cyber and privacy, our founder Bastian Purrer interviews one of the most creative entrepreneurs in business, Bart Decrem. As a long time entrepreneur in both for-profit and non-profit sectors, the average internet user might recognize Decrem from his achievements at Disney Mobile Games and Mozilla Firefox or from Tapulous, the company that invented Tap Tap Revenge.
SSOs: a simple solution to the password problem?
For most of the internet’s history, we have interfaced with goods and services online by using multiple username-password combinations. These have often proved complicated for both users and firms. They’re complicated for users because these combinations are difficult to remember, or they may use the same combo for different services, consequently minimizing security.
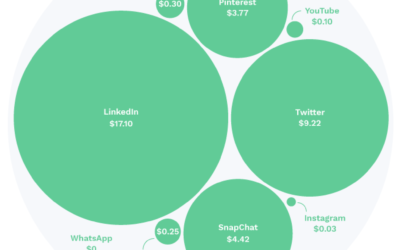
What is data monetization and how does it use personal data?
Maybe you were looking up the price for a new flat-screen television. Or maybe you decided to reorganize your pantry and searched online for some food storage containers. Within a few hours, your social media feeds started showing advertisements for televisions or BPA free containers. We’ve all been through this. It’s not that hard to figure out what happened. Somewhere in cyberspace, little packets of information are constantly being added to a secret and very personal profile about you and your habits.