Why App Security is More Important Now Than Ever
By Alan Zu
October 19, 2020
What is the most important part of an application? Depending on who you ask, the answer might be different. User experience? The features? The in-app purchases?
These three things share one thing in common. None of them are the correct answer.
The most important part of an application, especially in contemporary times, is application security. What is it? Application security describes security measures at the application level that aim to prevent data or code within the app from being stolen or hijacked.
Application security has always been an essential part of applications, both during development and post-development. Although arguably it wasn’t always the most vital component of an application, in light of recent developments, application security has slowly become one of the most important, if not the most important part of an application.
Why? To answer that, let’s explore the importance of application security and how the application industry addresses it.
Now, you might think that most, if not all, sensitive corporate data should be relatively secure. Maybe it would just be the smaller companies that lack security, as they might not have the resources necessary to plug any holes in their security. But unfortunately, this paradigm does not match with reality. An estimated 43% of all data breaches are traceable to application vulnerabilities. One of the largest data breaches that ever happened to Capital One was when Paige Thompson exploited a web application to access hundreds of millions of consumers. To add to this massive horror show of publicity, Capital One is expected to suffer anywhere from $100 million to $500 million in costs due to the sensitive nature of the data.
With this increasingly interconnected system, why is app security even more important now? For starters, given the ever prevalent digitization of our world, the amount of data that will be available to hackers will only grow exponentially (especially given the circumstances that surround COVID-19, at least in the USA). But there’s still quite a few not-so-obvious reasons as to why it will progressively become essential to our world.
The Faults in App Security You Should Know About
There’s this concept known as “security debt” that application security firms like to use. Basically, web applications tend to have security flaws, but not all of them are solved within a given time for whatever reason. This means that going into the next year, there will be some pile of unaddressed security issues that remain unsolved. This is what security debt refers to. And just like how corporations are almost always in debt, corporations also always seem to be in security debt. The result of this is that only 56% of all security flaws are addressed, and only 76% of all severe security flaws are addressed. And don’t think that these flaws can be fixed overnight either. It takes anywhere from around 70 to 20 days to patch a flaw, which leaves potentially a colossal window for hackers to exploit it.
As a whole, this makes it so that about two-thirds of all applications do not pass industry guidelines
So far, everything I’ve talked about seems somewhat disconnected, especially if you’re not in the industry of web security, so allow me to make this more material. Did you notice that I never defined “severe security flaws”? Truth be told, there’s no non-arbitrary way to describe what “severe” means, so I believe it would be best to illustrate with an example. Since everyone either has or is currently using Zoom, I’ll give a few examples of severe security flaws that Zoom once had.
While it is not unheard of for social media platforms to gather data on a user’s medical condition, such as in one cancer patient’s court case against Facebook, it is from these first two categories that most data is gathered. Each platform has their own specific bits of data that they want to get from users, but there is a general pattern that nearly all sites share.
Zoom had three notable security flaws, all within the last year:
- On Windows systems that had Windows 7 or older operating systems, a foreign user could execute arbitrary code (essentially giving a foreign user complete control over a device ) via an exploit.
- It was possible to create and send a special .gif file through Zoom chat that allowed a foreign user to execute arbitrary code.
- A user could send a .zip file through Zoom chat that allowed a foreign user to execute arbitrary code.
Notably, in these cases, users had no input in whether or not they were hacked. Gone are the days where being hacked meant opening suspicious files. This means that regardless of how diligent people were in attempting to prevent security breaches, there was absolutely nothing they could do to prevent foreign users from interfering with their computers. Couple these potentially extremely harmful security issues with Zoom users not using the security options available to them, and corporations could have lost millions of dollars worth of information. Thankfully, Zoom has fixed all of these issues and made it much more difficult for unauthorized users to enter rooms, but that isn’t to say that there won’t be future issues.
Mobile Applications: The Bottom of the Barrel
The big kicker is that what I’ve talked about so far only deals with desktop applications. It’s important to address the other type of application that’s on the market: mobile applications. According to this graph by Business Insider, the smartphone market has been increasing over the past few years. And with this new technology market available, there is, of course, an abundance of mobile applications to fill that demand.
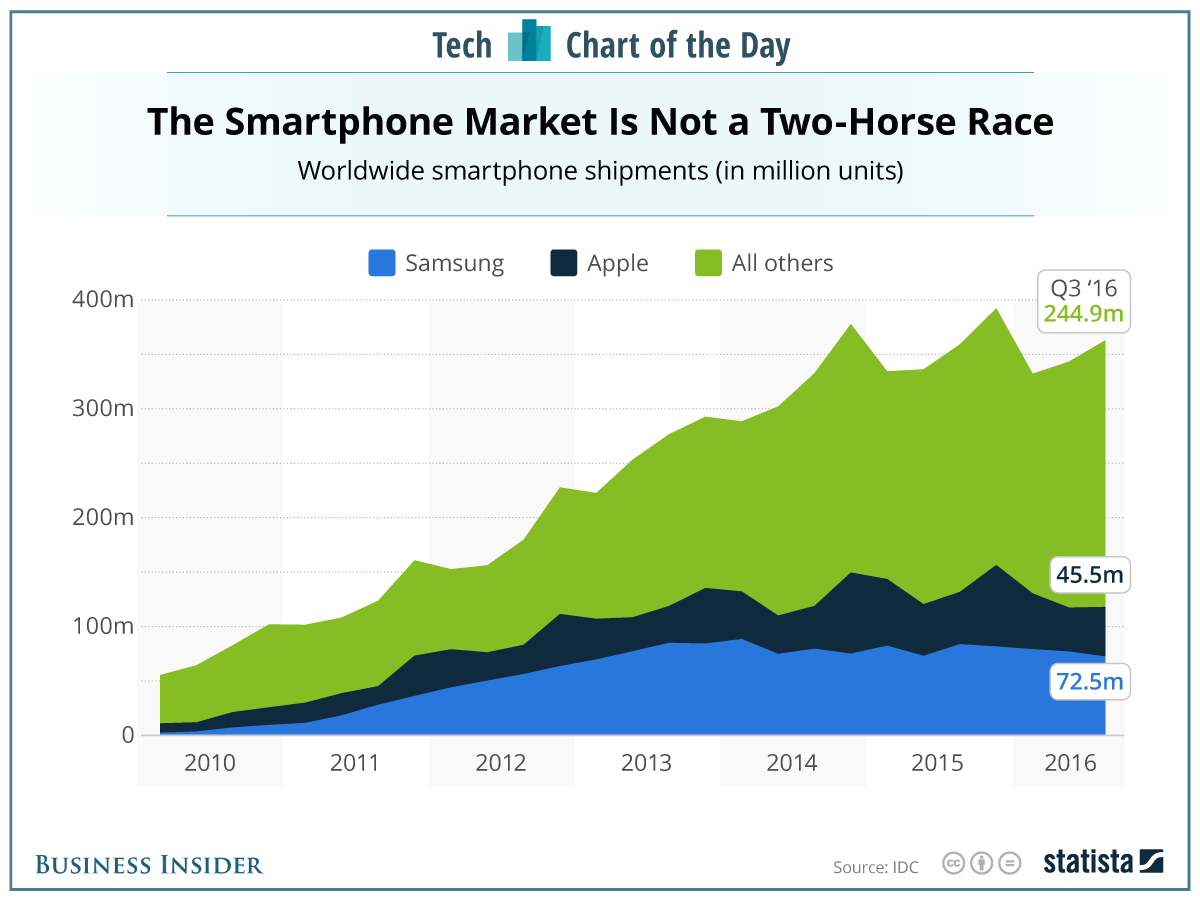
Yet unfortunately, mobile application devs are often not up to par in the security department. This is extraordinarily problematic as society becomes more and more reliant on mobile devices. According to a study conducted by Arxan using publicly available tools (such as APK Extractor), it took an average of only 8.5 minutes to breach 30 different mobile applications via over 180 different critical vulnerabilities.
Here are some absurd statistics on how terrible mobile application security is:
- 97% of the applications lacked binary protections, which made it possible to reverse engineer the code
- 90% had unintended data leakage
- 83% had insecure data storage, which made it possible to breach the application via an API attack
- 80% had weak encryption
- 70% had insecure random number generation, making it rather easy to break into sensitive data via guessing
And these aren’t small issues that could be swept under the rug. Most, if not all, of these flaws can lead to breaches in sensitive data. The fact that so many of these apps are missing a number of these data protections seem to suggest that there is a systemic lack of rather basic security measures being implemented. This is further corroborated by the fact that many corporations still do not have a specific budget allocated towards mobile app security.
These stats imply that the industry has a major problem on its hands. It’s not too much of a stretch to say that our lives are slowly becoming more and more dependent on mobile device applications. Just how many of these applications are ticking time bombs just waiting to explode and cause millions, even billions of dollars, in damages? If we’re going off of Arxan’s study, most of the mobile applications we use fall into this category. If that’s the case, it can only be a matter of time before we see the next big data breach.
What to Keep an Eye On
According to Trustwave Spiderlabs Managing Consultant Mike Park, poor application security comes from four things. Two of these things come from the developer’s end: Developers are generally more interested in features than security and developers often fully understand the platform that they are using. If you’re reading this, chances are that this information is pretty useless to you. And while it is a little depressing to know that a sizable portion of applications have serious security issues, the good news is that you, as a consumer, do at least have control of what applications you use.
The other two things that Mike Park theorized contributed to poor application security are from the consumer’s end: Most consumers know next to nothing about application security and are very gullible. So, the best way for consumers to make applications more secure, is to know the applications and the corporations behind them. While there is a systemic lack of strong application security within the industry, this is only an average. There are many companies that recognize the importance of application security and strive to make their applications as breach-proof as possible. However, it’s not always obvious which corporations operate under this agenda, and those that do are often not the most popular options. Therefore, do some research and actually go through the trouble of finding an application that provides a safe experience. It may be a bit more work than you’d like for just downloading an app on your phone or PC, but that small bit of work could really save not just you, but potentially millions of others from much more trouble.


