How to Protect Your Online Information
By Evan Walters-Zucco
August 13, 2021
The pandemic has created a lot of issues, both in the real and virtual world. As a result of increased remote work and online activity, cybercrime has risen an alarming 400% in 2019 and 2020 combined. Ransomware also rose 69% in 2020. There has also been a rise in non-cyber crime-related online security concerns as of recent. These include actions taken from large corporations and even governments. Thankfully, there are a myriad of ways you can protect your online information.

Rising Security Risks
The news is often filled with headlines highlighting concerns about online security and privacy. Apart from the before-mentioned cybercrime threats, the concern of government surveillance has become increasingly apparent since Edward Snowden’s 2013 leaks. This behavior has persisted despite being exposed. Recent reports state that the U.S. government has attempted to contract the emails of four New York Times reporters while also seizing their phone records from 2017. Aside from the government, internet users also have to worry about corporations recklessly collecting and using their personal information and data. Facebook, Microsoft, and Google have all had multiple high-profile data breaches within the last couple of years, adding to the concern of data security and privacy. Consequently, it has never been more important than ever to protect your online information. Thanks to new technologies, it has also never been easier to do so.
Browsers
Browsers are usually the first step to securing online privacy. This is mainly because of the reputation of the Tor Browser; Tor is synonymous with online privacy and security. Tor is most often thought of in connection with the ‘dark web’. Dark web browsing is the antithesis to cybersecurity if done incorrectly. Consequently, prior Tor research should be done before preemptively downloading it onto your device to avoid illegal activities and websites. However, Tor notes that many of its users are people concerned about online privacy, people who want to avoid censorship, journalists and activists who require anonymity and privacy, and even government agents. Although Tor adds a significant amount of anonymity and privacy in comparison to Google Chrome, Safari, or Microsoft Edge, it is not bulletproof. Tor should be used in conjunction with the later suggestions to best protect anonymity and your data.
While Tor is the most well-known privacy browser, Brave Browser is a fantastic alternative. With Brave, users can earn the native cryptocurrency of the browser, Basic Attention Token ($BAT), through enabling ads. Brave is built on the same open-source Chromium project as Google Chrome but instead encrypts user data and avoids Google’s servers. Most importantly, Brave does not collect your online data, even with ads enabled; this is what truly separates Brave from Google. Brave also has a privacy mode that enables Tor through their browser. Overall, Brave is a fantastic alternative to Google Chrome and Microsoft Edge, and it even allows you to profit off of ads instead of the corporations. Unlike ads for Chrome and Edge, Brave ads function as notifications. This is because Brave is built with an Adblocker, and you have to turn on ads to see them in Brave. Adblockers, in general, are an added protection against fake news and malware, while also saving bandwidth. However, like Tor, Brave is not the only step to protecting your online privacy and should be used in combination with the other steps.

Search Engines
Search engines are an often overlooked factor in protecting your online privacy. Search engines like Google and Bing collect an obscene amount of data for each user. The data they collect is practically churned into profit. Google made a staggering $30B from Google search in Q1 2021. Using a search engine that does not profit off of your data is essential for privacy and protecting your online information.
For search engines, DuckDuckGo is the household name for privacy. DuckDuckGo (United States) is regarded as one of Google’s largest competitors. Despite this, Google still captures 92.05% of all searches. However, DuckDuckGo is highly regarded for a reason; it is the default search engine for Tor and can be chosen for Brave, Chrome, and Edge. DuckDuckGo protects users by blocking advertisement trackers, thus eliminating targeted ads. Furthermore, while using this search engine, there is no online profile created as you browse. Essentially, DuckDuckGo cannot collect your data and use it to drive profit. DuckDuckGo in combination with Tor or Brave is a fantastic way to bolster your online privacy and anonymity.
Although DuckDuckGo is the most popular privacy search engine, there are other quality, lesser-known options. Qwant (France) does not collect user data and has clearly defined guidelines that protect user privacy. MetaGer (Germany) and Swisscows (Switzerland), are two other great search engine alternatives. Swisscows is arguably one of the most secure search engines as they run their servers in a secure bunker, and do not record any data. Everything they do is kept separate from the European Union and the United States, making your data more secure than ever. Qwant, MetaGer, and Swisscows all secure user privacy while simultaneously providing optimal search results.

Usernames and Passwords
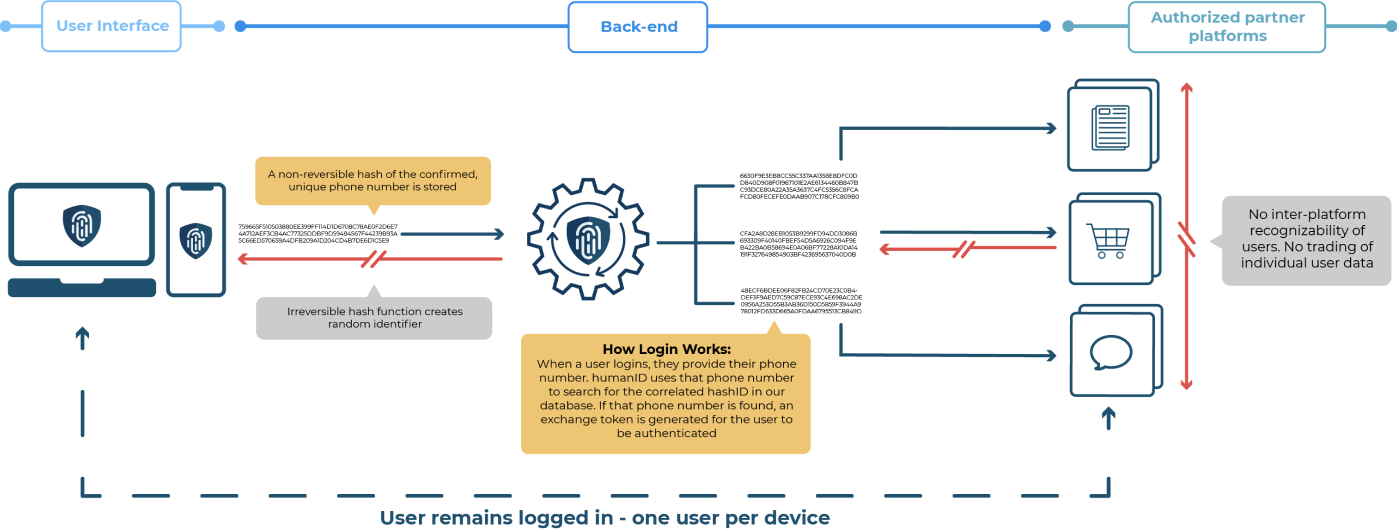
In regards to protecting your online information, the typical advice is to have different, long, and cryptic passwords. However, that is increasingly difficult with multiple emails, social media accounts, and other logins. A staggering 51% of people use the same passwords for their personal and work accounts. Utilizing the same password for each account allows for a hacker to access your whole digital life. Usernames and passwords also present a unique opportunity for cybercriminals to access your accounts. Having multiple accounts increases the security concerns as you essentially are carrying more targets on your back. To combat this, we as humanID have created a one-click anonymous login solution that secures the user’s online privacy and security.
We are successfully implemented in the Japanese whistleblowing app Ninja Anon, a free speech site called Polarizer.io, and a workplace rights-based app GreenZone. We protect our user’s privacy by never collecting any data or personal information, and deleting the data upon authentication. We are also less susceptible to data breaches in comparison to other companies due to double hashing. Also, by eliminating the need to store unnecessary usernames and passwords, humanID offers a significantly reduced chance of being hacked. In combination with the other suggestions, humanID offers a fantastic option to secure your anonymity and online data.

VPNs
Virtual Private Networks (VPNs) are amongst the most popular and trusted ways to protect privacy and anonymity. VPNs are a crucial part of protecting your online privacy as it creates an encrypted tunnel for your data. This is important for two key reasons: it protects your data from cybercrime when using wifi, and it shields your data from internet service providers who can sell it to third parties. VPNs also hide your IP address, which is your device’s online identification. With your IP address, someone could access your general location, disable certain online services, access your online identity, and potentially hack your device or steal your identity if your device is insecure.
Fortunately, there are many fantastic VPN options for privacy. NordVPN and ExpressVPN are two excellent, reputable VPNs that have stood the test of time. Aside from the generally known VPNs, Orchid offers a fantastic alternative that is decentralized. By being decentralized, Orchid prevents data logging. Decentralization is the distribution of power several others away from a central authority. Logging is mitigated by providing multiple hops between providers. Essentially, it is extra insurance in case the VPN is secretly logging. Orchid functions differently because it is built on Ethereum, a blockchain platform that functions as a decentralized public ledger. Users configure a circuit in Orchid by first setting up an account and then funding it with its native token, $OXT. The app then connects the user to the Orchid network and selects a node to serve as the VPN. Payments for bandwidth are done through a stream of continuous OXT nano payments. Overall, VPNs are arguably one of the best ways to secure online privacy and anonymity, but like everything else, they should be paired with the other steps for the best results.
Protecting your data is not something that only journalists and social activists should care about, it applies to everyone. With data now being largely considered the most valuable asset, corporations will likely expose your data in pursuit of profit. This puts your data in danger due to greed alone. To make sure your data is not recklessly abused and even leaked, it is important to follow the steps above and take calculated precautions while using the internet.
