Defining Hashing and Encryption
By Helena Miller
September 15, 2021
Hashing and encryption are two common methods that are imposed to enhance digital privacy. It is necessary that enterprise users understand the purposes, functions, capabilities, and limitations of each method.
What is hashing?
Hashing integrates the translation of a provided key into a code and the substitution of a hash function with a recently generated hash code. Hashing is the procedure of taking a string or input key, a variable produced for storing narrative data, and representing it with a hash value. In general, hash values are determined by algorithms and have much shorter strings than the original ones. Hashing utilizes algorithms that are used to convert the amounts of data of a file into a much shorter value that has a fixed length. This value stands for those strings in a coherent, efficient way. This process facilitates the ability to verify whether a user’s data is revealed to the right person.

What do hashing and encryption do?
To reiterate, hashing utilizes algorithms that convert data into a much shorter value or key of a fixed length that represents those strings. This is how hashing gives people the power to control what information users cannot get access to and utilize. Such capabilities enhance the administration of hashing when it is adopted by companies. The most popular algorithms that are used to apply hashing are MD5, HMAC, and SHA.
- Message Digest 5 (MD5) is an algorithm that facilitates the breaking down of data into smaller, more manageable amounts for companies. For instance, an MD5 hash can be depicted as 32 hexadecimal characters rather than 128 bits.
- Hash-based Message Authentication Code (HMAC) is another algorithm that can be used to improve the integrity of the internet. HMAC is unique in that it employs a shared secret key to add some randomness to the result so that only the sender and receiver know the key. In this manner, using HMAC is more dependable than using the other algorithms.
- Secure Hash Algorithm (SHA) is likewise used to enhance the integrity of the internet. Three kinds of SHAs are utilized to break down data for employers: SHA-1, SHA-2, and SHA-3. SHA-3 is the most versatile type of SHA because it can break down data into the smallest possible unit. This capability can make it easier for companies to acquire access to valuable information while enabling each company to remain anonymous on the internet.
Like hashing, encryption is also a very helpful method to improve the security of internet users. Encryption can do many things. Not only can it enable a company to remain anonymous online; but, it can also be used to protect its data from becoming tampered with, know who they are communicating with, and sign online documents. Arguably the most helpful kind of encryption is end-to-end encryption. End-to-end encryption is a procedure in which only the sender and the intended recipient can read the message. No third-party entities know the encryption key. A commonly used end-to-end encryption communication service is WhatsApp. When one is using WhatsApp, the end-to-end encryption makes sure that just the two communicators can read or listen to what is being digitally transmitted and no one else, including WhatsApp. This occurs because when one uses end-to-end encryption, one’s messages are fixed with a lock. When this happens, only the recipient of the message and you hold the special key required to unlock and understand the messages.
How do hashing and encryption differ?
Hashing and encryption are similar in that they handle the data, messages, and information effectively and can convert data into numerous formats. However, the function and design of these processes differ. To simplify, encryption is a two-way function that utilizes encryption and decryption while hashing is a one-way function that converts a plain text into a unique digest that is impossible to reverse. Encryption is used to improve people’s security so that each person’s fragile data cannot be accessed by cybercriminals, hence supporting data confidentiality and security. It demands a private key to convert the function’s encrypted text into plain text. If the sole authorized entity has the key, encryption does this by encoding easy text that is visible to it. Hashing is used to create random strings that avoid the copying of data. Through this process hashing verifies the integrity of the content by identifying the existence of every modification and changes to a hash output.

What security advantages and issues do hashing and encryption address?
Hashing and encryption have many security benefits. Most importantly, it is a lot easier to find a record after the data has been hashed. For example, hashing makes it easier for companies to find an SSL certificate because hashing does not copy people’s information from databases. Second, if somebody compromises a database, that person becomes incapable of doing anything immediately with the hashed passwords; there are no easy ways to recover the original passwords. Third, hashing is useful to compare the information of two files or a collection of them. People can apply hashing without comparing all of the files. As for encryption, it is used to encode information so that just the authorized party can read it. When the person possesses the right key, that key will be used to decrypt the data into a readable message.
It is a better idea to use both hashing and encryption instead of one of these methods because the security will be much more efficient. For instance, using HTTPS will make sure that any password delivered over the internet cannot be accessed by anyone observing the connection. It manages this by using a hash to keep the password in the database. This ensures that the computing system break-ins will not present further compromises to each company due to passwords being reused and other reasons.
Even though hashing and encryption have many benefits, they each have a few restrictions. For example, the output of a hash function cannot be reverted back to the input with an efficient algorithm. However, this does not mean that it cannot be cracked because databases that have hashes that contain common words and short strings can be easily seen by people through Google searching. Also, common strings can be easily and rapidly brute-forced and given access to with a dictionary attack.
Today’s technology may not make encryption capable of happening. This is because the encryption of data depends a lot on the nature of the unused data and in conjunction with the strong authorization and access controls. By letting only authorized users by limiting their access to the principles of least privilege and executing on the fly decryption of data upon access, companies are given a minimal level of encryption of data in use. When hackers get access to a network, but cannot get authorized access with valid credentials, encryption will protect data from being read, copied or manipulated. However, cyber incidents facilitated by gaining unauthorized access to systems with valid user credentials, like phishing scams and social engineering, can enable hackers total access to the decrypted data.
Hashing focuses on creating random strings to avoid copying of data kept in databases. humanID uses hashing to protect user data by inserting a phone number into a hash function. This way, a user’s phone number gets stored properly. After this happens, the hash function generates a random identifier. As a result, inter-platform recognizability of users and the trading of data between users does not occur online. There is one internet user per electronic device because only one person stays logged into the account or application.
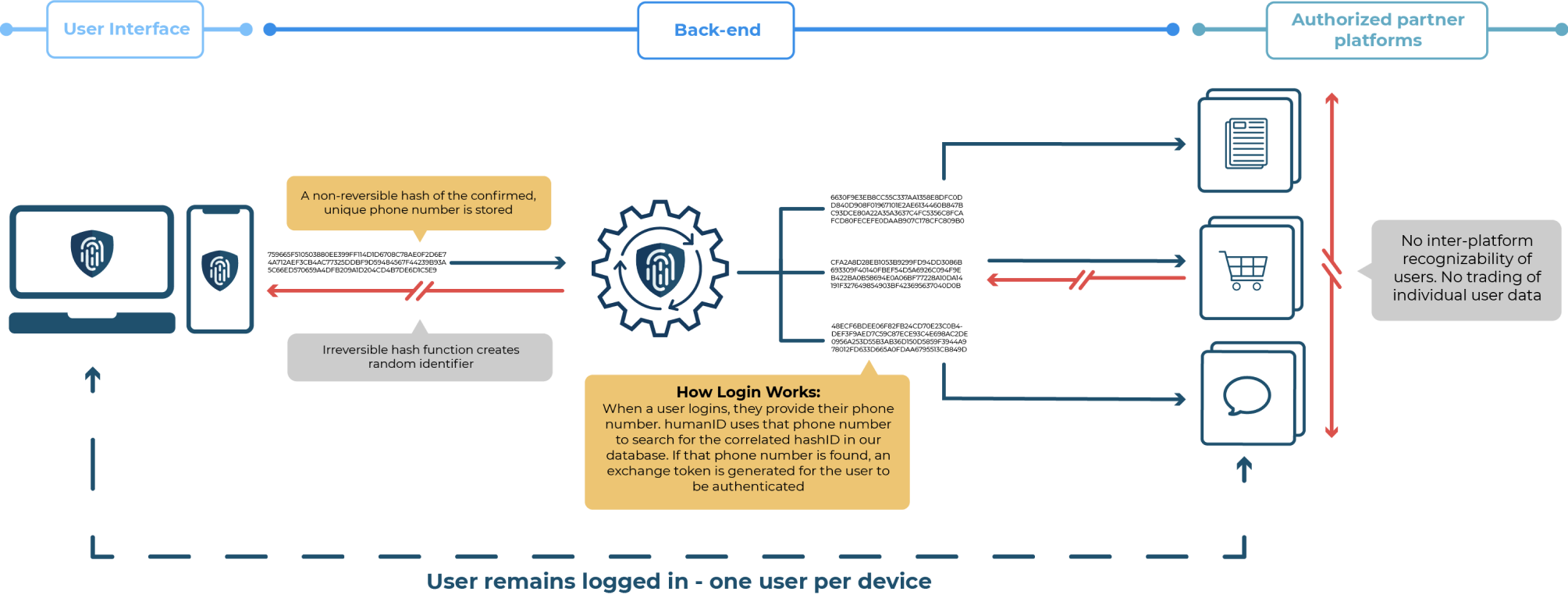
Overall, hashing and encryption both improve security and privacy but with varying intentions and functions. Since hashing can be used to prevent bots, spammers, and abusive users very effectively, hashing can be more effective to protect user data than encryption.
