4 Alternatives to Passwords
By Caroline Wang
April 12, 2021
Chances are you’ve had to log into a password-protected account or device within the past couple days. Whether it’s an email account or your phone, you probably find yourself entering a predetermined, secret password quite often. Passwords are supposed to authenticate that the user behind the login actually owns the account. However, many technology brands are seeking alternatives because passwords present two major problems. If a password is easier to remember, it is deemed weak and easy to guess. Thus, access to the account by a second party is more likely to be granted. Conversely, if a password is strong and complex, chances are that the user will forget the password themselves. As a result, the search for password alternatives, especially by major technology companies, has increased.
Two-Factor Authentication
Two-factor authentication (2 FA) requires the user to input two separate keys to gain access to the network. Unlike the typical username-password login, 2 FA adds an additional layer of security by adding another question. This question is typically answered using a specific pin number or password that only that specific user should know. For example, when making purchases with a debit card, a user’s pin number would be the second authentication factor. The pin is something that only that user should know, allowing them sole access to the usage of the card.
Another form of 2 FA is the usage of a second network resource to gain access to an account or device. This typically requires a user to confirm their sign in on a separate resource before accessing the account of the attempted login. There have been increasingly more instances of this form of 2 FA, one of which is from Apple. If a user signs into another device using their unique Apple ID, the user will automatically get a notification to verify their login using a pin on their previous device. However, Apple’s 2 FA is enabled in settings by choice, so this is only active if a user enables it. However, Apple’s 2 FA cannot be disabled once a user has enabled it for over two weeks. Apple claims that this is to fully protect your information since 2 FA has become a more relied upon security measure.
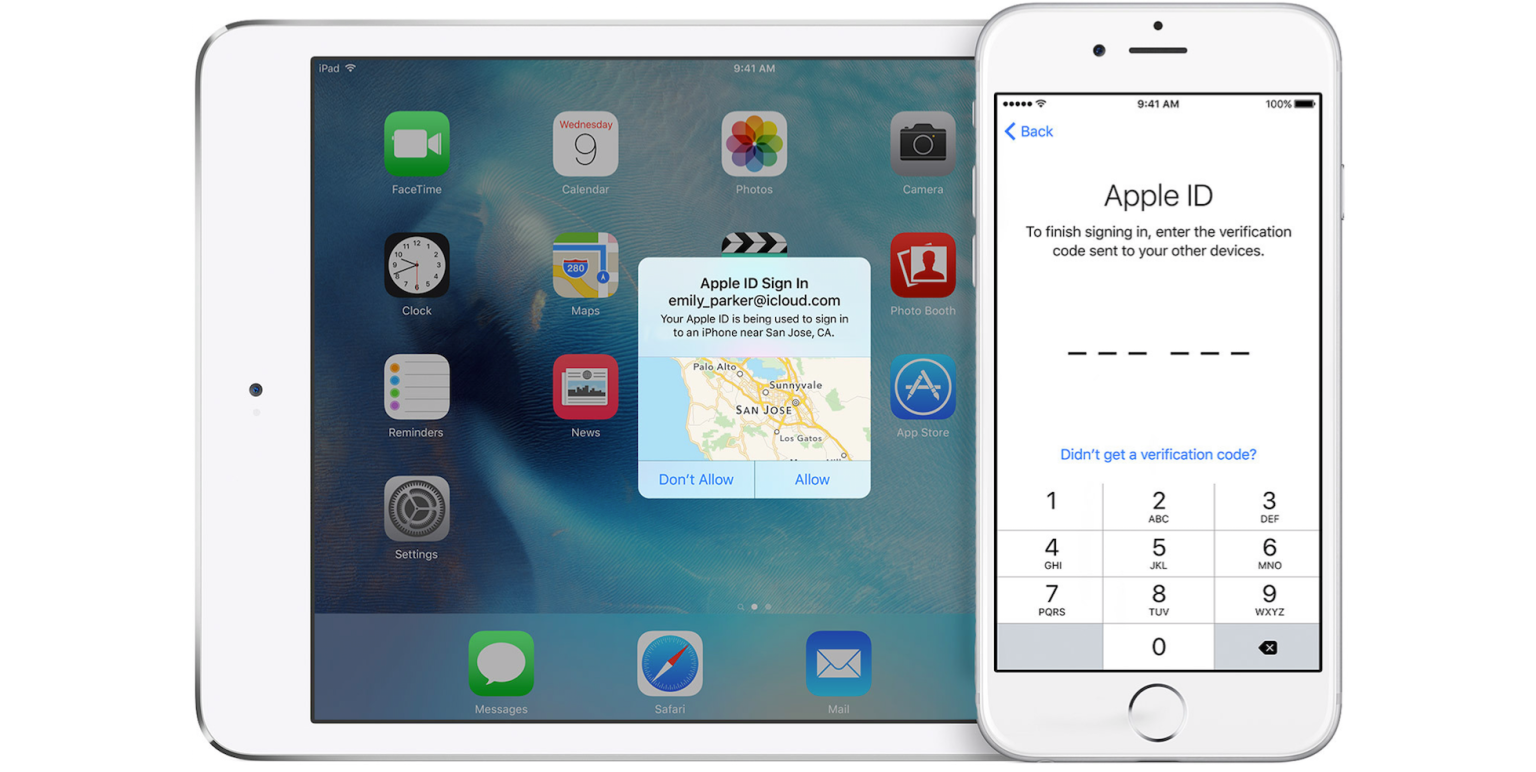
Another form of 2 FA utilizes a third-party service to ensure an extra layer of security to a login. Many university logins have started using DUO, a 2 FA service that requires a user to authenticate themselves by connecting their phone to their accounts through the DUO Mobile app. Upon submitting the correct username and password, DUO prompts the user to choose a method of authentication from three choices. The first and most commonly opted for option is for the user to send a push notification to their phone’s app. The notification asks for permission to verify this login as their own before allowing access to the account. Similarly, the second option DUO provides is for the user to incite a phone call to their own phone. Upon picking up and verifying the login through simple instructions, the user gains access to their account. The final method is to enter a pin number that DUO Mobile provides in its app. These pins are randomly generated each time the user requests a login. Thus, it ensures that only the user can access the account. DUO provides a great example of 2 FA in work as a third-party system. Companies or institutions can purchase this product to have a multitude of verification factors for their network logins.
Fingerprint Identification
The fingerprint alternative to passwords is a form of biometric authentication. Biometric authentication utilizes a user’s unique, physical feature to identify who they are. Thus, a fingerprint, a feature that no two individuals have in common, is an alternative way of identifying a user. Rather than having the user manually input a password, a fingerprint identification saves the user time, as well as the potential frustrations with forgetting a passcode and having to reset it.
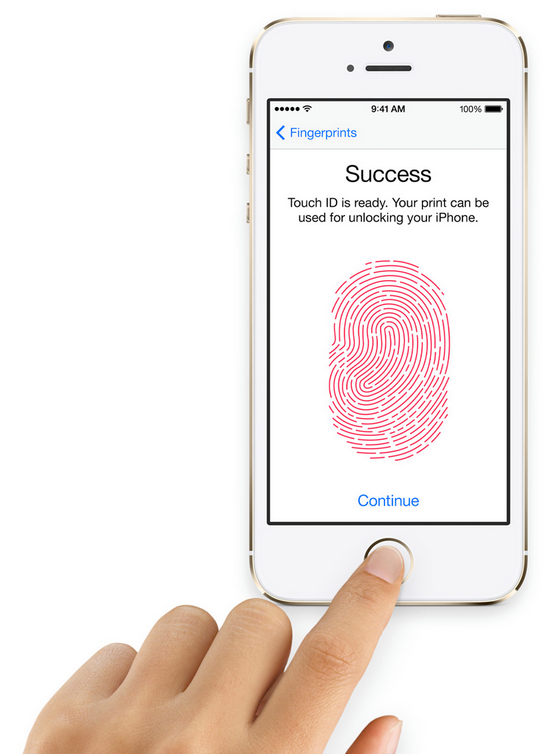
In 2013, Apple launched its first devices that included Touch ID, a form of user identification for its devices that utilizes a fingerprint. Built within the home buttons on this wave of devices were a series of sensors under the finger pad. These sensors capture a high-resolution image of the user’s fingerprint from the subepidermal layers of the skin. Touch ID is able to analyze this unique image with acute precision. This allows for the device to accurately identify the correct user for each login and ensure that no other user can access the device unwarranted.
In 2013, Apple launched its first devices that included Touch ID, a form of user identification for its devices that utilizes a fingerprint. Built within the home buttons on this wave of devices were a series of sensors under the finger pad. These sensors capture a high-resolution image of the user’s fingerprint from the subepidermal layers of the skin. Touch ID is able to analyze this unique image with acute precision. This allows for the device to accurately identify the correct user for each login and ensure that no other user can access the device unwarranted.
Following Apple’s release of TouchID, Samsung announced its own fingerprint ID for its devices the following year. Rather than using fingerprint sensors, Samsung implemented ultrasonic technology that transmit ultrasonic waves to capture a fingerprint’s uniqueness. Samsung claims that their technology has a higher recognition rate than Apple’s Touch ID due to its ability to work in temperature variant environments. This prevents a user from struggling to unlock their device via fingerprint in outdoor settings.
Facial Identification
Facial Identification is a second form of biometric authentication that analyzes a user’s unique facial mapping to identify them accurately. Just four years later, in 2017, Apple launched its first mobile devices with Face ID as a replacement for Touch ID. The primary motive for this was behind the new iPhone X’s design, which would not have the usual home button that housed the Touch ID sensors. Thus, Face ID became Apple’s new biometric authentication technology.
Apple’s Face ID works by mapping the geometry of a user’s face using a TrueDepth camera system. The TrueDepth camera adds an infrared emitter that patterns over 30,000 dots over a user’s face. These dots are differentiated by proximity, which maps out a user’s facial features. Because each user’s facial recognition should be unique, the device can differentiate its rightful owner from any other people that may pick up the device. Thus, facial recognition acts as a password alternative.
Microsoft was able to combine all of the mentioned password alternatives above into one software program called Windows Hello. The program allows users to utilize a second pin number, fingerprint, or facial identification to sign into their PCs. Microsoft’s goal with implementing password alternatives was to increase security and reduce inconvenience for its users. With technologies that are more difficult to breach, a user can ensure that their devices and accounts are more secure than with a simple password.
humanID
humanID is a one-click, anonymous login solution that ensures a safer online experience by ensuring each user’s privacy and anonymity. The idea behind the technology is that each user is assigned a single, non-reversible identifier for every application a user logs into. humanID’s mobile and web applications allow users to sign onto third-party websites with their unique phone number. Each user’s phone number is hashed in the process, creating a randomly generated identifier that is irreversible to the original number. The data is instantly deleted after verification and humanID never shares any information with their partners. Through humanID’s technology, any user can be certain that their logins are protected, and that their information is safe. Thus, humanID’s quick and convenient technology ensures the safety of all users of the community without the hassle of remembering a password.

