
by Design Lead | Dec 9, 2020 | Cybersecurity & Risks, Posts
Holding Hospitals Hostage: An Overview of Ransomware Attacks on Hospitals and Healthcare Systems By Sean Wang December 9, 2020 As hospitals continue to increase their array of interconnected machines and software to care for and manage patients, they become...

by Design Lead | Dec 7, 2020 | Digital Identity, Posts
Designing Digital Identity By Vishal Venkatesh December 7, 2020 Personally identifiable information can be any data that helps identify a person. The more uniquely identifiable the data is, the more sensitive it is said to be. Features that are used to identify people...

by Design Lead | Dec 2, 2020 | Login & Authentication, Posts
Password vulnerabilities and mitigations By William Pardi December 2, 2020 Passwords are one of the most common forms of authentication in today’s very technological world, and for good reason. They are easy to set up and use, and for a lot of applications, are...
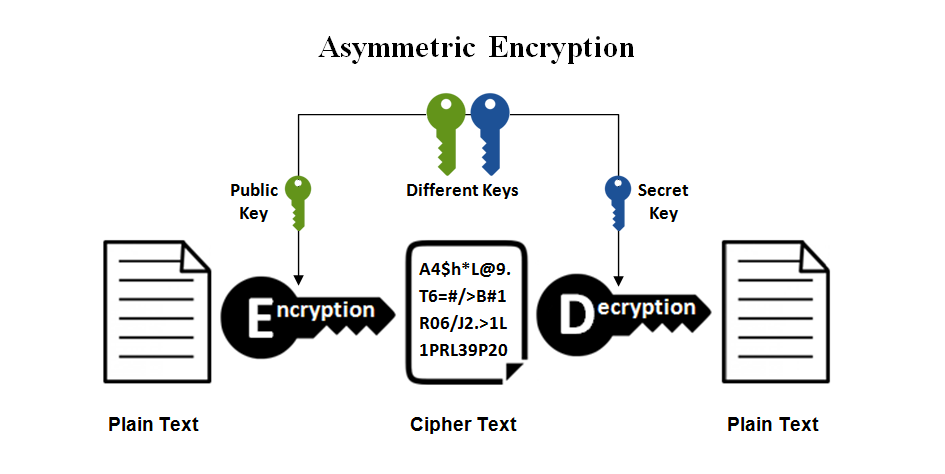
by Design Lead | Nov 23, 2020 | Cybersecurity & Risks, Posts
What is Encryption? By Anagha Arvind November 23, 2020 Any phone call you make, text message you send, item you purchase online, or bill you pay for, uses some form of encryption to protect your identity and maintain your privacy. The roots of encryption can be traced...
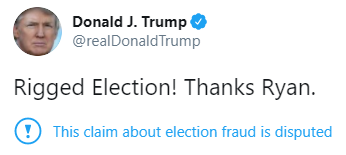
by Design Lead | Nov 18, 2020 | Data Protection & Privacy, Posts
Disinformation and misinformation: why the distinction matters By Jacob Hanna November 18, 2020 If you’ve been on the internet for any amount of time, you have likely seen something — be it a news article, a social media post, or whatever else — which...

by Design Lead | Nov 16, 2020 | Posts, Social Media
FAANGS Out: What big tech wants with your data By Lorence Olivo November 16, 2020 Tech companies love to collect data on their users. Our personal data is a hot commodity for companies that want to optimize their services, sell something, or keep you as a returning...







