7 Social Media Sites and their Data Breaches
They say your data is protected, but how have they measured up?
By Lorence Olivo
October 26, 2020
In a previous article, we talked about how social media companies harvest a large quantity of data from the people who use their services. Monetizing data is how sites like Twitter and Facebook make most of their income, but these services have tried to promise users that their most private and compromising data is never sold or made vulnerable. In this article, we will explore times when these social media platforms have failed to adequately secure our data.
It seems like we’re always hearing about how some tech site has been hacked or how a voter database has been leaked online. If the 11,000-plus data breaches in the past 15 years have shown us anything, it is that any information that we share online is at risk of being compromised, if it hasn’t been already. The question that we have to ask ourselves, then, is how much trust do we really want to put in big tech to keep some of our most compromising data safe?
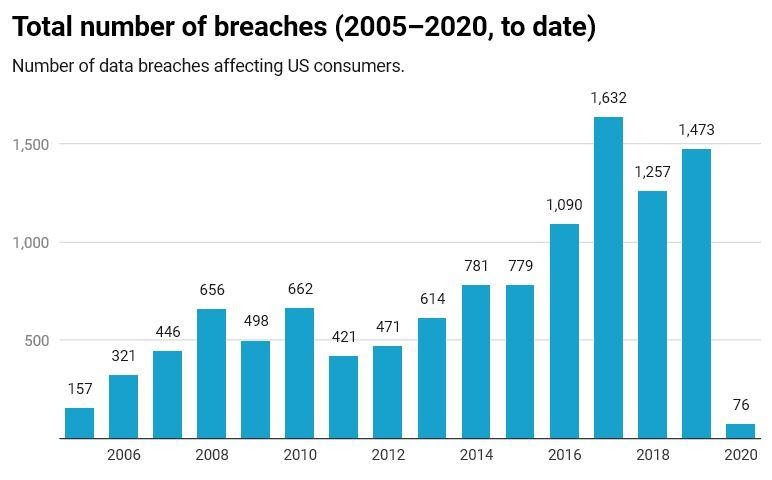
It might seem like a question that is not worth asking in our modern world. Whether we like it or not, the world has become interconnected and humans have become increasingly dependent on social media outlets to function in society. This doesn’t mean that we have no control over the security of our data. In this article, we will look at 7 examples of social media platforms and the data breaches that they have suffered over the past ten years to see what kinds of vulnerabilities are most common and what methods we as users can employ to better protect ourselves.
What data is on the menu?
When we start talking about topics such as data breaches and compromised accounts, it is important to stop and take a moment to define some terms to get a better picture of what we are talking about.
As stated above, social media platforms harvest a wealth of information from their users. Despite its broad range, the categories of data commonly stored can be broke down as follows:
- Information in the public profile: name, location, etc.
- Contact information: email addresses and sometimes phone numbers.
- Uploaded content: such as public posts, private DM messages, photos, and videos.
- Usage data based on what links you interact with (links to the platform and from the platform).
- Data on which devices are linked to which accounts (phone, tablet, computer)
- Facial recognition data.
- Metadata on where and when people log in or use a platform
Only some of this data is ever anonymized and sold to advertisers or utilized to improve consumer experiences. Things like email addresses and phone numbers are supposed to be kept secure. Yet the fact remains that these bits of information are still on file. If the wrong people gain access to that kind of information, much of our personal life could become compromised.
It’s an unfortunate truth that this kind of information does get out far too often. Thousands of people suffer from their accounts getting compromised every year through malware, phishing scams, and other nefarious means. Much of this can be accounted for by simple, user-side errors, such as reusing the same passwords or clicking on a link that they shouldn’t have. But social media companies are not off the hook, either, and below we’ll talk about 7 social media companies who have suffered data breaches and how many people might have been affected as a result.
1) Snapchat – Estimated affected: Upwards of 4.6 million users
The 2013 “Hack”
At the end of 2013, hackers of a site called SnapchatDB.info posted the account information of 4.6 million Snapchat users. Usernames and sometimes even phone numbers of users were available to the public for download. In a statement to TechCrunch, SnapchatDB said that they breached Snapchat to urge the company to tighten its security measures.
“Our motivation behind the release was to raise the public awareness around the issue, and also put public pressure on Snapchat to get this exploit fixed. It is understandable that tech startups have limited resources but security and privacy should not be a secondary goal.”
The hackers explained that they accomplished this data breach by using an exploit created in the app’s most recent update. The exploit had been discovered a week prior by Gibson Security, an Australian-based “white hat” hacking group, who went public with the vulnerability in the app’s Android and iOS API.
Soon after the breach, Snapchat wrote in a now-deleted blog post that the vulnerability was not a major concern and that some measures had been put in place to make a second data breach “more difficult to do.” As both Gibson Security and SnapchatDB would later follow up, these changes were “very minor obstacles” and could be easily circumvented to still take advantage of the exploit.
The Employee Spies
Most people are aware that social media sites sell information to advertisers or use collected data to better improve their services. It’s how these sites make most of their money. But even in these situations, we’d like to hope – and these platforms would like us to believe – that social media sites are able to adequately protect our anonymity and keep any personal information safe from hackers. But what if it isn’t hackers who are trying to spy on us? What if it’s instead employees of the company itself?
In 2019, an article released by Motherboard detailed how Snapchat employees had been repeatedly spying on their users. Thanks to a special company program called SnapLion, employees were able to gain access to the location, phone number, email address, and even saved Snaps of their users. SnapLion was originally supposed to be a tool used to gather information on users in response to valid law enforcement requests. As anonymous employees from within the company revealed, however, there were individuals across various departments within the company that had access to the program and were actively using it to spy on users.
While current employees have emphasized Snapchat’s efforts to improve user privacy and limit abuse of privileged access such as through the introduction of end to end encryption, this kind of reveal provides a sobering message that we would do well to keep in the forefront of our minds. Social media platforms are products we use daily while inadvertently giving away much of our data. Once that data is stored online, it is only as secure as the people who work at these social media companies believe it to be.
2) Twitter – Estimated Affected: 32 million users (with another 330 million suspect)
The Russian Job
In 2016, the account information of over 32 million Twitter accounts was supposedly compromised by hackers. LeakedSource reported in a blog post that they had received a copy of the compromised data from a hacker known as “Tessa,” who was part of a group of Russian hackers responsible previously for major data breaches such as Myspace and LinkedIn (both discussed below). The compromised cache contained about 32.9 million records that included email addresses, usernames, and passwords.
Twitter responded by stating that their systems had not been breached but that they were actively attempting to check their data against what was being shared online. There was speculation that the accounts could have been compromised as a result of malware on Firefox and Chrome browsers, but ultimately the data was more likely the result of users recycling email and password information from their Myspace and LinkedIn accounts that could have already been compromised. Some merit does seem to support this claim as high-profile individuals like Facebook CEO Mark Zuckerberg became the targets of ridicule for reusing simplistic passwords like “dadada” for multiple sites.
Ultimately, it is difficult to know the full extent of damage done during this “breach,” but it serves as one of many red flags for users trying to keep their information safe, and as just one out of several breaches to Twitter that would come in the following years.
The Glitch in the Code
In 2018, Twitter released a statement to its more than 330 million users to immediately change their passwords after a bug in their updated code exposed these passwords in plain text. Plain text refers to normal, everyday language. When a database records passwords like this, it means that there has been no encryption and anyone who can gain access to the database can see these passwords.
The bug occurred due to an issue in the hashing process, the system by which passwords are masked through the replacement of their characters with a random string that gets stored on Twitter’s system. The bug made these stored passwords be displayed in plain text in Twitter’s internal log, which it claimed to have discovered on its own and resolved. No one’s information should have been compromised by hackers, but the company still urged users to make changes, highlighting how it could be a factor as simple as human error that results in a major data breach.
The Bitcoin Scam
Twitter dismissed the 2016 breach as nothing more than hackers taking advantage of people using the same passwords, for multiple accounts. They claimed the 2018 breach was false because the glitch that revealed user passwords was only done so on their internal logs. In 2020, however, Twitter could no longer make excuses to gaps in their security when the platform was compromised by a severe cyber attack. Earlier this year, hackers were able to perform a targeted attack on 130 high-profile “verified” Twitter accounts in a Bitcoin scam hack. Individuals like Bill Gates, Jeff Bezos, and former Vice President Joe Biden had their accounts seized by hackers. The hackers were able to impersonate these individuals through tweets to their followers in a scam for money. This breach only gave access to the compromised accounts for a few hours, but it is reported that the hackers made nearly $118,000 through Bitcoin donations while the scam was active. Through these accounts, it is believed that the hackers were able to deliver their scam to an audience of at least 350 million people.
While the exact nature as to how the breach occurred has not been revealed, Vice journalist Joseph Cox has raised the possibility that a Twitter employee could have been involved in the incident and leveraged their powerful internal Twitter tools to achieve such a feat.
Whatever the cause, the implications for one of the world’s most important communication systems to be compromised in such a quick and damaging manner raise questions for what contingencies might be needed or are already put in place to prevent hackers from taking control and manipulating such a large audience in the future.
3) Instagram – Estimated affected: 49 million users
The Unlocked Door
Facebook has always had a rocky history in preventing data breaches, but2019 was a particularly bad year for the company.Breaches of both Facebook and its subsidiary site Instagram exposed sensitive data of at least 49 million users.
Unlike other data breaches that companies have suffered, the case behind how Instagram’s data was compromised is a curious one and has become part of a growing threat to data security. The data was not compromised due to an attack on Instagram’s servers, nor was it due to a leak in their system code. The data was not even stolen from the Instagram network.
The culprit? Unprotected marketing company servers.
There are many companies that lack the resources to run dedicated — and costly — server hardware. To answer the needs of these companies, Amazon Web Services (AWS) was developed as a cloud-computing product that could host company apps, websites, or databases. Instagram originally ran much of their infrastructure through AWS, but when Facebook purchased the company back in 2012, it switched Instagram over to a dedicated and more secure server.
It was on one such AWS server, however, that a Mumbai-based marketing company called Chtrbox stored sensitive data that it had gathered on Instagram users and left unsecured, without a password, for at least 72 hours.
It’s not a large amount of time, but it provided many opportunistic hackers free access to data gathered from Instagram accounts, primarily that of major influencers, with roughly one in twenty accounts being compromised.
No financial information was compromised in the breach, but it did allow hackers to pull information such as their bio, profile picture, number of followers, their location by city and country, as well as their personal contact information (email address and phone number).
4) LinkedIn – Estimated affected: 167 million users
Damage over time
Back in 2012, the popular business social network reported it had suffered a data breach after 6.5 million passwords were leaked onto a Russian hacker forum. The hackers had apparently been able to “crack” the hashes that LinkedIn used to cryptographically scramble user passwords. While certainly a large number of potentially compromised accounts, the company never clarified exactly how many accounts had actually been affected. It was only years later that the full extent of the breach was revealed.
In 2016, a hacker known as “Peace,” who was part of the initial hack back in 2012, started selling records for somewhere between 117 and 167 million LinkedIn user records on the illegal black market website TheRealDeal. Findings reported that these records included email addresses, hashed passwords, and LinkedIn ID numbers. LinkedIn was quick to make a statement that it recommended users to enable two-step verification on their accounts but would notify users individually if their accounts had been compromised.
What made this situation a major concern for LinkedIn users was the realization that either LinkedIn never knew how damaging the 2012 data breach was or that they had known but remained silent until the information went public.
5) TikTok, Instagram, and YouTube – Estimated affected: 235 million users
Why do you need three copies of the same unprotected data?
You might be curious as to why this breach covers three separate social media platforms, one of which we’ve already talked about. Surely they don’t use the same system to store their information, right? Luckily they don’t. As you’ll soon find out, however, this was not the fault of any direct breach in their systems. Once again, an unprotected marketing company database is to blame.
Back in August of this year, a Comparitech report was released concerning Social Data, a data brokerage company that sells data on social media influencers to marketers. Comparitech researchers were able to uncover three unprotected IPv6 database addresses which each held identical copies of the exposed data. Of the 235 million social media profiles, they were broken by platform as follows:
- 96,714,241 records from Instagram
- 95,678,713 records from Instagram
- 42,129,799 records from TikTok
- 3,955,892 records from Youtube
Each record also contained some or all of the following information:
- Profile name
- Full real name
- Profile photo
- Account description
- Whether the profile belongs to a business or has advertisements
- Statistics about follower engagement, including:
- Number of followers
- Engagement rate
- Follower growth rate
- Audience gender
- Audience age
- Audience location
- Likes
- Last post timestamp
- Age
- Gender
Comparitech was able to get their findings to Social Data, with the CTO shutting down the servers hosting the data around three hours later. There appears to be some suspicion as to the relationship between Social Data and another company known as Deep Social, which Facebook had already denied access to their platforms back in 2018.
6) Myspace – Estimated affected: 360 million users
Who would’ve thought to go after them?
For most people today, Myspace is something that probably never crosses their mind, unless they wish to think back to the early 2000s. While many might have forgotten it – or maybe never even heard of it at this point – the social media site serves as a reminder that user data never truly disappears.
In 2016, Myspace suffered one of the most damaging data breaches to date when over 360 million accounts were compromised.
From a report by LeakedSource.com, the data breach contained mostly old data from before new security features had been added back in 2013, but it still consisted of email addresses, passwords, and in some cases a second password. The site reported that there were over 427 million total passwords available for sale.
Myspace was quick to take action, however, and invalidated the passwords of affected accounts. The biggest risk to those account holders would be if they used those same login credentials on other accounts—something that identity thieves often check.
7) Facebook – Estimated affected: nearly 2 billion users
We’ve saved the best (or worst) for last.
Facebook has been the subject of numerous controversies over the years. They just can’t catch a break. But when you see a track record of data breaches as long as Facebook’s, pity is not the first feeling that one feels.
Facebook has a history of data breaches going as far back as 2013 when the company announced they had inadvertently exposed 6 million users’ phone numbers and email addresses over the course of a year (which they argued was never exploited maliciously). The data leak was the result of a glitch when Facebook users tried to download the contact info for their list of friends, acquiring more information than they were supposed to receive.
The two worst years for Facebook, however, wouldn’t come until 2018 and 2019. Over these two years, Facebook would suffer around 7 data breaches, compromising around 1.9 billion users. A full account of each individual breach would take up an entire article on its own. A list with that goal can be found here. Suffice it to say that the breaches were the cause of everything from technical glitches, hacker exploitations, improper storage of user passwords in plaintext files, user records being stored on public servers (multiple times), and more.
Conclusion – Only you can protect your data.
With the number of data breaches that happen to social media sites, we have to accept that these platforms are not capable of keeping our information secure. So what can be done to keep things protected?
If you don’t want to delete your social media accounts, the best thing to do is delete any information that could be used against you. Don’t use the same passwords across all of your social media accounts and don’t share any of those passwords with more sensitive account profiles (banking, business, school, etc.). Two-factor authentication is another feature that could be your best friend in these situations.
If you’re looking for another way to keep your data safe, but without the need of a small book’s worth of unique passwords, humanID could be the solution for you. Our goal is to provide everyone with ONE anonymous, safe, and protected digital identity. As a non-profit, social sign on service, users can enjoy security and speed when browsing their favorite sites without the worry of having their email or passwords being leaked.
